Exploit — Bash Shellshock Part 1. In September 2014, when a single…, by ka1d0
Por um escritor misterioso
Last updated 03 julho 2024

In September 2014, when a single security bug in Bash was disclosed there was chaos in the security community. This bug allowed attackers to escalate privileges and execute arbitrary code on a remote…
GitHub - xdistro/ShellShock: :octocat: Shellshock is a vulnerability in GNU's bash shell that gives attackers access to run remote commands on a vulnerable system
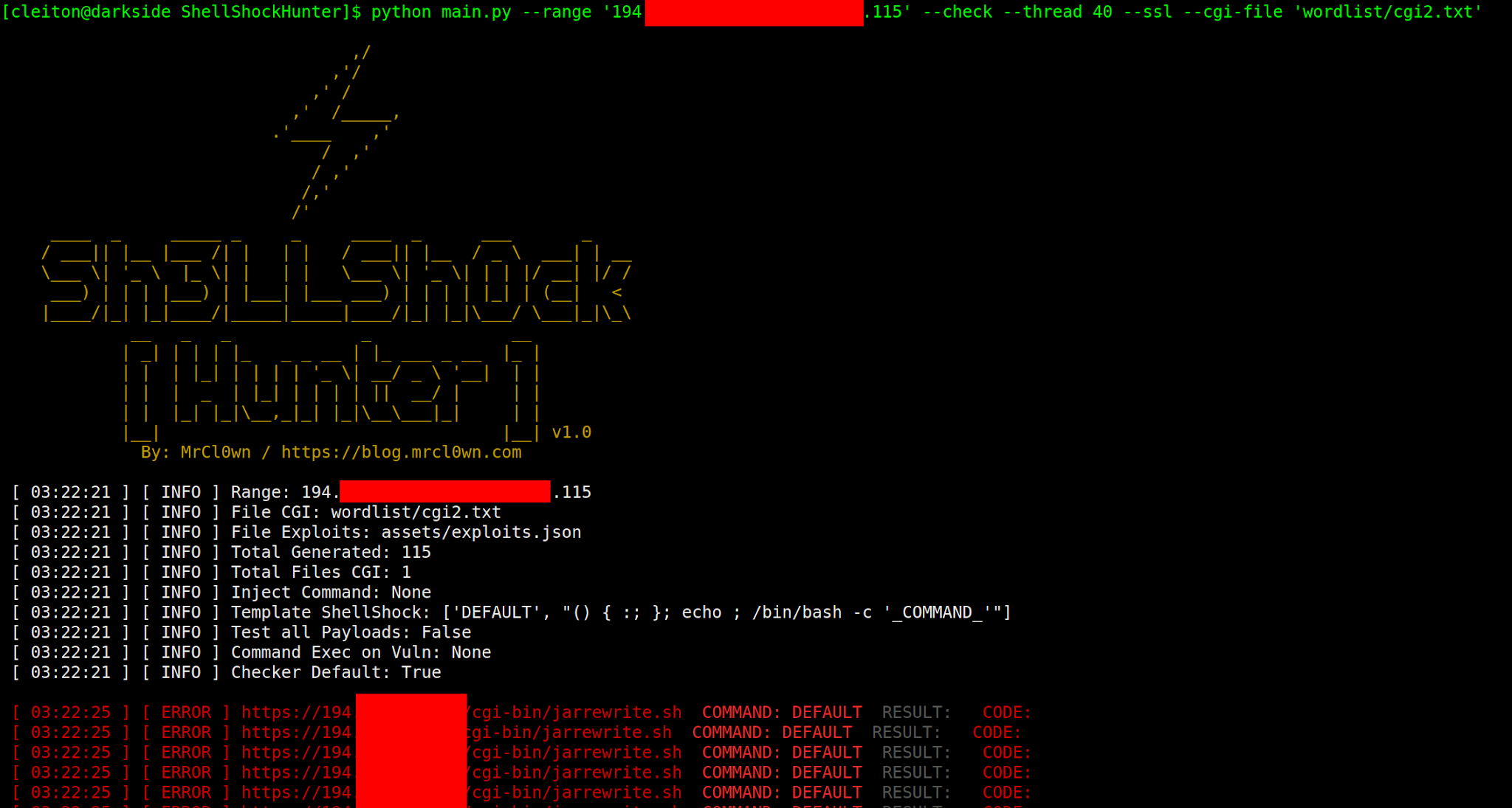
ShellShockHunter - It's A Simple Tool For Test Vulnerability Shellshock
Pentesting — VulnHub: DC-1. This post is one of the many that I'll…, by ka1d0
Bitcoin Blockchain as a Graph in Neo4j, by ka1d0

Shellshock

Shellshock Vulnerability and Attack

The Shellshock Attack: University of Delhi, Lucideus Technologies, PDF, Software
PentesterLab: Learn Web App Pentesting!
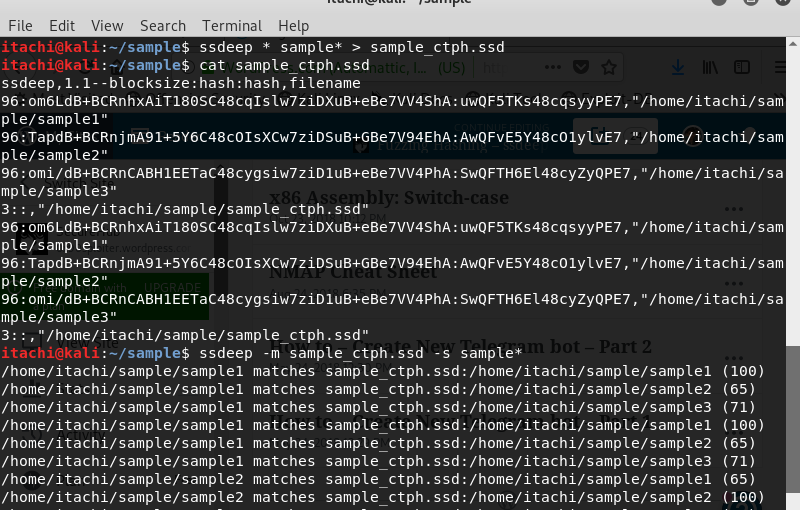
Threat Attribution using ssdeep. We have all used cryptographic hashes…, by ka1d0
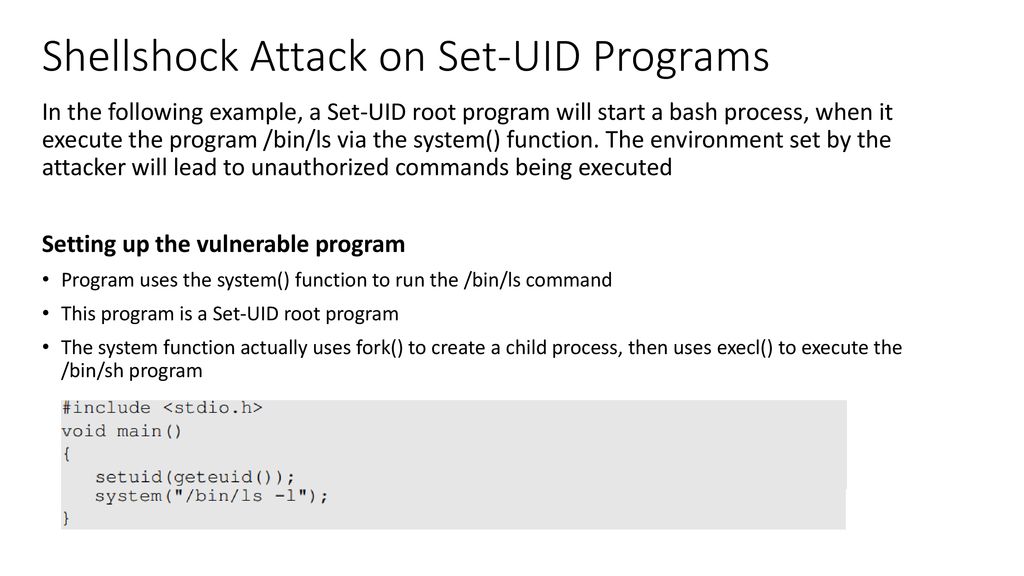
SHELLSHOCK ATTACK. - ppt download

Endpoint Protection - Symantec Enterprise

Return-Oriented Programming — ROP Chaining, by ka1d0
Malware Analysis — Gozi/Ursnif Downloader, by ka1d0
Shellshock Bash Vulnerability

Shellshock Bash Bug Vulnerability Explained
Recomendado para você
-
 Hack the… Pulley - LEGO® Technic™ Videos - for kids03 julho 2024
Hack the… Pulley - LEGO® Technic™ Videos - for kids03 julho 2024 -
 The Internet Braces for the Crazy Shellshock Worm03 julho 2024
The Internet Braces for the Crazy Shellshock Worm03 julho 2024 -
 Hackers Are Already Using the Shellshock Bug to Launch Botnet Attacks03 julho 2024
Hackers Are Already Using the Shellshock Bug to Launch Botnet Attacks03 julho 2024 -
 Shellshock In-Depth: Why This Old Vulnerability Won't Go Away03 julho 2024
Shellshock In-Depth: Why This Old Vulnerability Won't Go Away03 julho 2024 -
 The evolving use of Shellshock and Perlbot to target Webmin03 julho 2024
The evolving use of Shellshock and Perlbot to target Webmin03 julho 2024 -
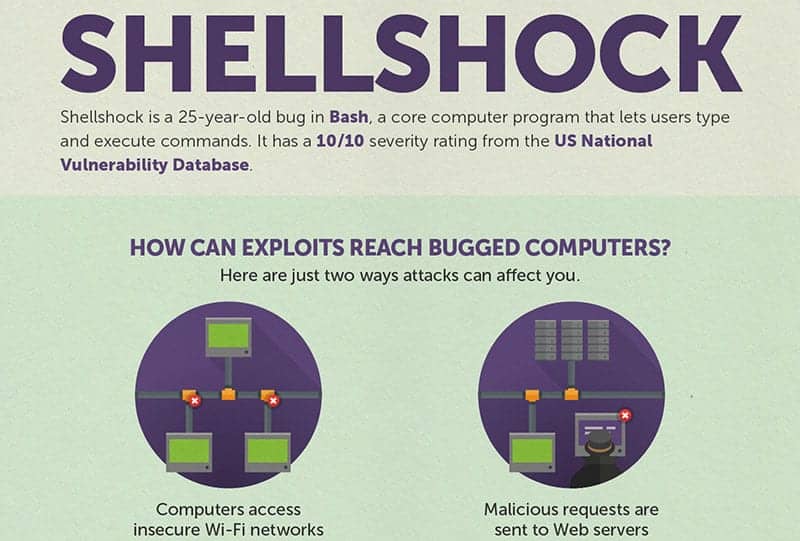 Shellshocked: Are You Prepared?03 julho 2024
Shellshocked: Are You Prepared?03 julho 2024 -
Shellshock Scanner - Zimperium – Apps on Google Play03 julho 2024
-
 Worm exploits Shellshock to infect QNAP systems03 julho 2024
Worm exploits Shellshock to infect QNAP systems03 julho 2024 -
 Lab: Blind SSRF with Shellshock exploitation03 julho 2024
Lab: Blind SSRF with Shellshock exploitation03 julho 2024 -
 Why Shellshock is bad news for the Internet of things - The Washington Post03 julho 2024
Why Shellshock is bad news for the Internet of things - The Washington Post03 julho 2024
você pode gostar
-
 The Scholastic Book Fair is Here! We're Blogging - Heilicher Jewish Day School03 julho 2024
The Scholastic Book Fair is Here! We're Blogging - Heilicher Jewish Day School03 julho 2024 -
 roblox.x.aesthetic (@robloxxaesthet1) / X03 julho 2024
roblox.x.aesthetic (@robloxxaesthet1) / X03 julho 2024 -
Hakken - Join us today at 7PM for the opening of tickets03 julho 2024
-
Shokugeki no Souma Season 3「 AMV 」Live Like a Warrior03 julho 2024
-
 RX 6800 XT vs RTX 3070 Game Performance Benchmarks (Core i9-10900K vs Core i9-10900K) - GPUCheck United States / USA03 julho 2024
RX 6800 XT vs RTX 3070 Game Performance Benchmarks (Core i9-10900K vs Core i9-10900K) - GPUCheck United States / USA03 julho 2024 -
 Brand that is known for manufacturing baseball and softball clothing and equipment Crossword Clue Daily Themed Crossword - News03 julho 2024
Brand that is known for manufacturing baseball and softball clothing and equipment Crossword Clue Daily Themed Crossword - News03 julho 2024 -
 Mari Tamaki 🇦🇶 [A Place Further than the Universe / Sora yori mo03 julho 2024
Mari Tamaki 🇦🇶 [A Place Further than the Universe / Sora yori mo03 julho 2024 -
 10 dead in suspected arson attack at KyoAni anime studio (UPDATED)03 julho 2024
10 dead in suspected arson attack at KyoAni anime studio (UPDATED)03 julho 2024 -
 When, Why, and How Runners Should Utilize Treadmill Running03 julho 2024
When, Why, and How Runners Should Utilize Treadmill Running03 julho 2024 -
El Gaton Cats Icon Pack - Google Play 上的应用03 julho 2024

