Abusing Exceptions for Code Execution, Part 2
Por um escritor misterioso
Last updated 15 junho 2024

In this article, we'll explore how the concepts behind Exception Oriented Programming can be abused when exploiting stack overflow vulnerabilities on Windows.

Why the C Programming Language Still Runs the World
Learn how to add Input Validation to a REST API with NestJS and Prisma

PowerShell Best Practices for Preventing Abuse - Cyber Gladius

FastJSON deserialization bug can trigger RCE in popular Java

Code of Ethics for Government Services Poster
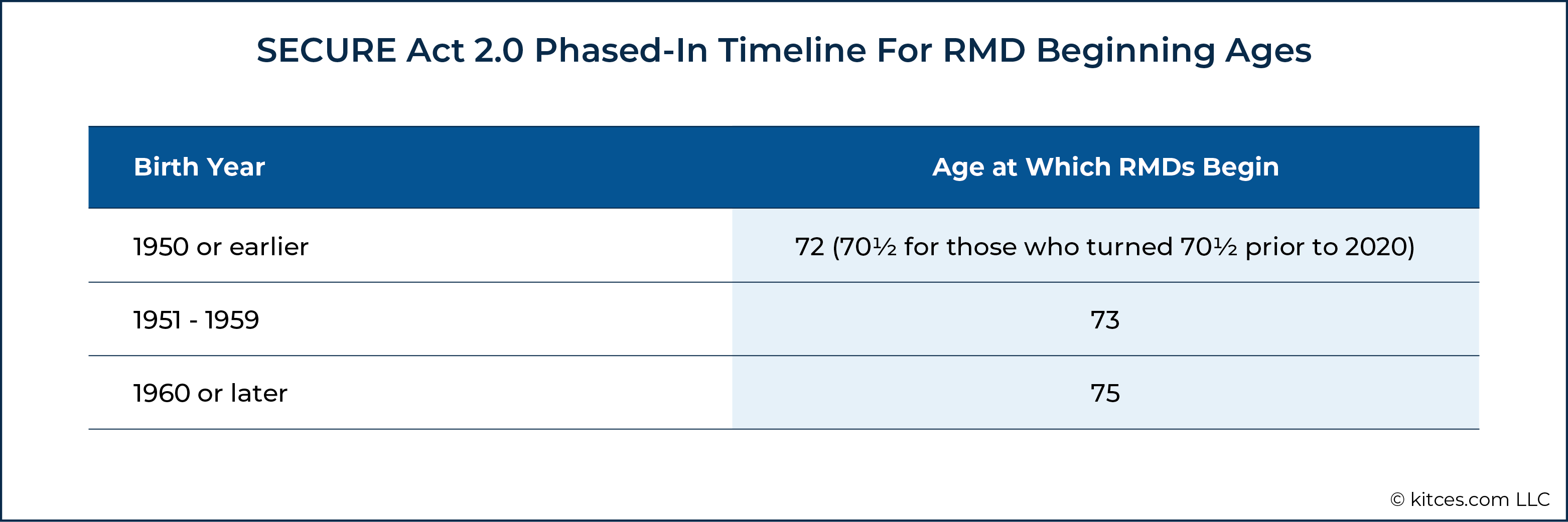
Secure Act 2.0: Detailed Breakdown Of Key Tax Opportunities

Coders' Rights Project Reverse Engineering FAQ
Smallscript - A Smalltalk-Inspired Scripting Language - CodeProject

How to Prevent and Deal With Referral Fraud and Abuse
Abusing Exceptions for Code Execution, Part 2

Project Zero: Remote iPhone Exploitation Part 2: Bringing Light
Recomendado para você
-
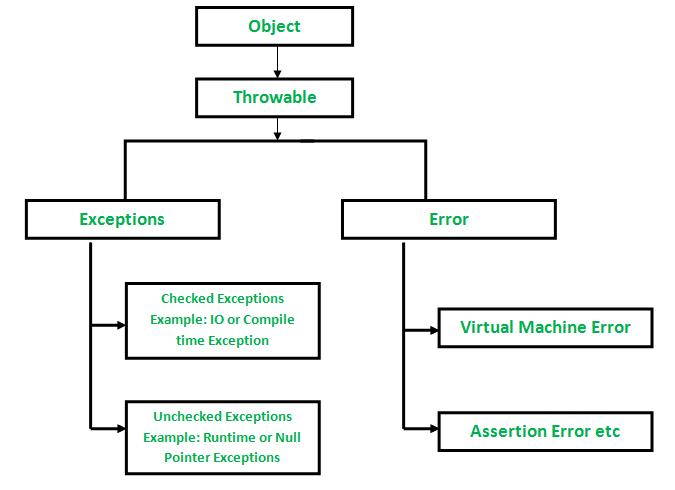 Checked vs Unchecked Exceptions in Java - GeeksforGeeks15 junho 2024
Checked vs Unchecked Exceptions in Java - GeeksforGeeks15 junho 2024 -
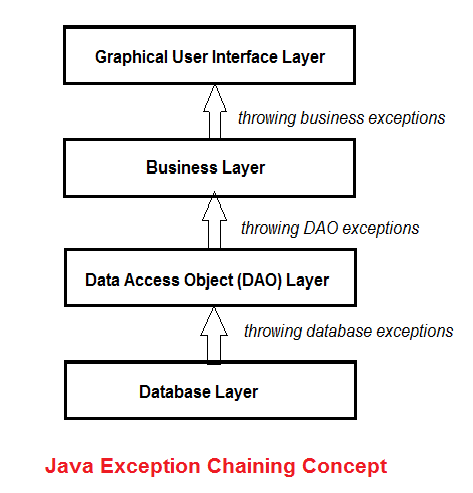 Understanding Java Exception Chaining with Code Examples15 junho 2024
Understanding Java Exception Chaining with Code Examples15 junho 2024 -
Types of Exceptions in Java15 junho 2024
-
 Python's raise: Effectively Raising Exceptions in Your Code – Real Python15 junho 2024
Python's raise: Effectively Raising Exceptions in Your Code – Real Python15 junho 2024 -
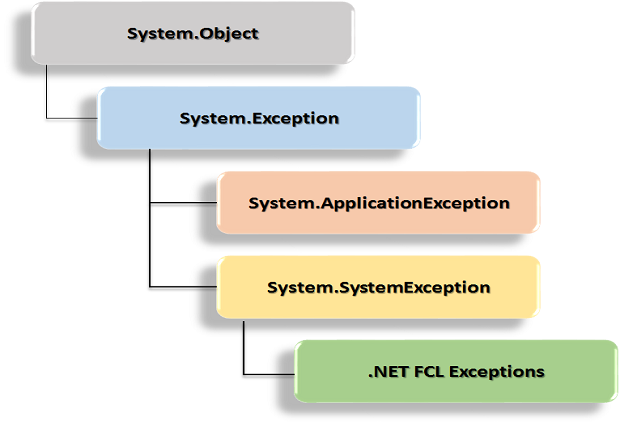 Best practices in handling exceptions in C#15 junho 2024
Best practices in handling exceptions in C#15 junho 2024 -
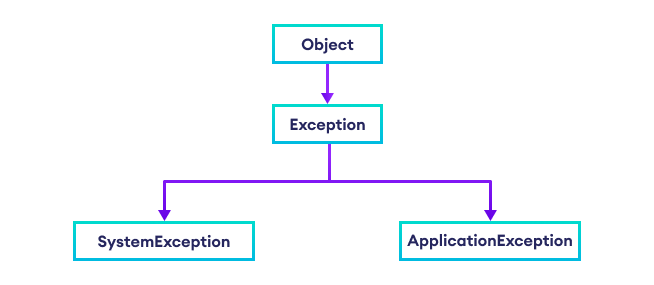 C# Exception and It's Types (With Examples)15 junho 2024
C# Exception and It's Types (With Examples)15 junho 2024 -
 HDA Publications – Exceptions Handling for DSCSA, Healthcare Distribution Alliance15 junho 2024
HDA Publications – Exceptions Handling for DSCSA, Healthcare Distribution Alliance15 junho 2024 -
![Exceptions API, Elastic Security Solution [8.11]](https://www.elastic.co/guide/en/security/current/images/exceptions-logic.png) Exceptions API, Elastic Security Solution [8.11]15 junho 2024
Exceptions API, Elastic Security Solution [8.11]15 junho 2024 -
 Exceptions in Snowflake Stored Procedures - ThinkETL15 junho 2024
Exceptions in Snowflake Stored Procedures - ThinkETL15 junho 2024 -
 java - Differences between Exception and Error - Stack Overflow15 junho 2024
java - Differences between Exception and Error - Stack Overflow15 junho 2024
você pode gostar
-
 Dark Souls II — The STL Smith15 junho 2024
Dark Souls II — The STL Smith15 junho 2024 -
![Safe to use] Top 5 Pokemon GO Spoofers for iOS & Android](https://images.wootechy.com/article/pokemon-go-spoofer.png) Safe to use] Top 5 Pokemon GO Spoofers for iOS & Android15 junho 2024
Safe to use] Top 5 Pokemon GO Spoofers for iOS & Android15 junho 2024 -
 GERENCIAMENTO DE INTEGRIDADE DE DUTOS (OLEODUTOS E GASODUTOS) - Abendi15 junho 2024
GERENCIAMENTO DE INTEGRIDADE DE DUTOS (OLEODUTOS E GASODUTOS) - Abendi15 junho 2024 -
 灵气稀薄我却修成大能漫画叫什么- 抖音15 junho 2024
灵气稀薄我却修成大能漫画叫什么- 抖音15 junho 2024 -
 UMPI ELO Coordinator Partners with High Schools to Bring Career Opportunities to Both College and High School Students – Maine DOE Newsroom15 junho 2024
UMPI ELO Coordinator Partners with High Schools to Bring Career Opportunities to Both College and High School Students – Maine DOE Newsroom15 junho 2024 -
 GIROS GRATIS DO DIA 26/09, FREE SPIN 26.09 em 202315 junho 2024
GIROS GRATIS DO DIA 26/09, FREE SPIN 26.09 em 202315 junho 2024 -
 Pokémon Sword & Shield - The Isle of Armor DLC Nintendo Switch15 junho 2024
Pokémon Sword & Shield - The Isle of Armor DLC Nintendo Switch15 junho 2024 -
 Hajime No Ippo : Law Of The Ring Season 4, First Look Poster15 junho 2024
Hajime No Ippo : Law Of The Ring Season 4, First Look Poster15 junho 2024 -
 TV Time - Kiss Goblin (TVShow Time)15 junho 2024
TV Time - Kiss Goblin (TVShow Time)15 junho 2024 -
 Ashley Graham-Resident Evil 4 by RodriguesD-Marcelo on DeviantArt15 junho 2024
Ashley Graham-Resident Evil 4 by RodriguesD-Marcelo on DeviantArt15 junho 2024
