IoT Botnets: Advanced Evasion Tactics and Analysis – Part 2
Por um escritor misterioso
Last updated 04 julho 2024

Nozomi Networks Labs analyzes new modification techniques malware authors use to evade detection and analysis tools.
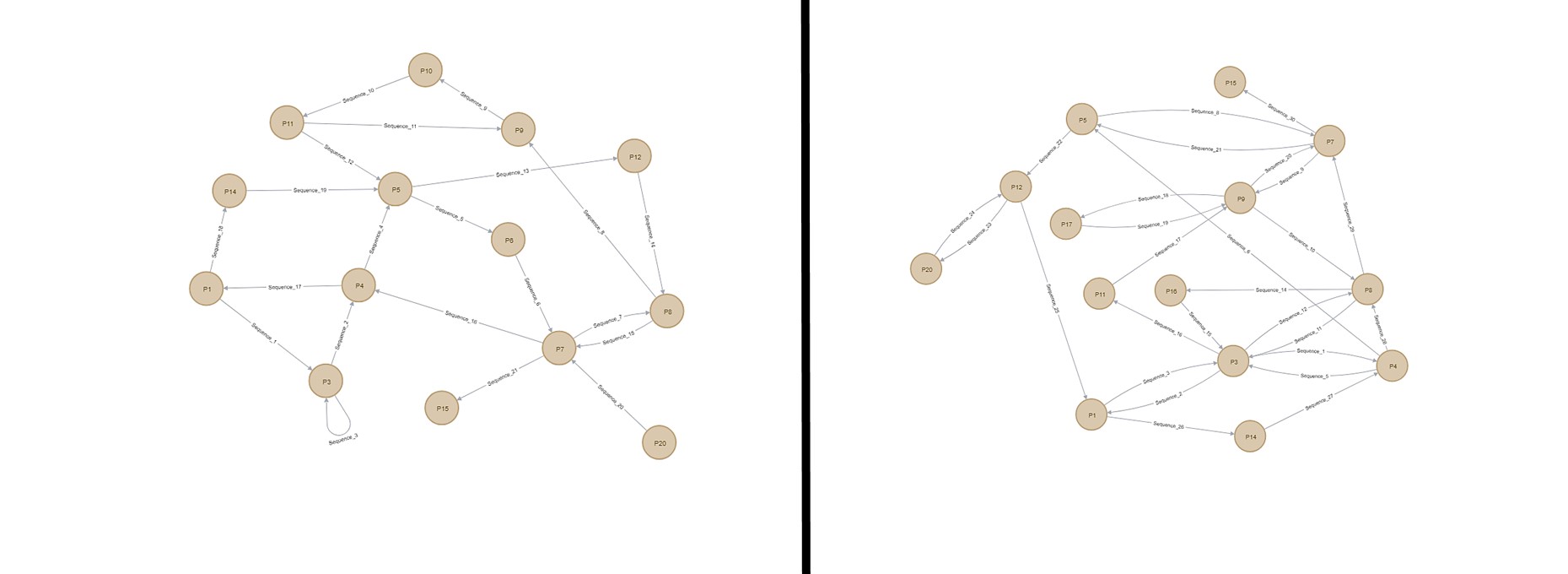
Identifying malicious IoT botnet activity using graph theory
Diagram showing how scans from a Mirai botnet result in attempted

DNS-based anti-evasion technique for botnets detection

IoT Botnets: Advanced Evasion Tactics and Analysis – Part 2
PDF) Botnet Detection Techniques: A Comparative Study
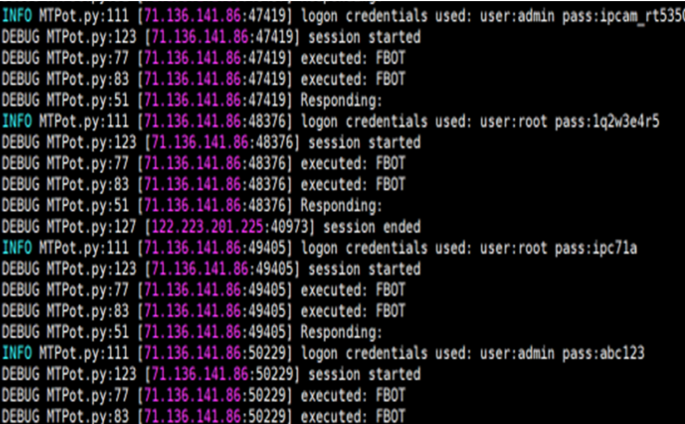
Detecting and confronting flash attacks from IoT botnets

How IoT Botnets Evade Detection And Analysis
Groups & tactics — Elastic Security Labs
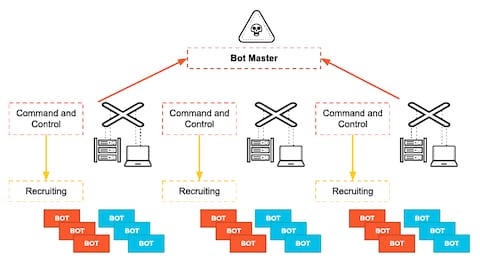
What is a Command and Control Attack? - Palo Alto Networks

IoTEnsemble: Detection of Botnet Attacks on Internet of Things

Botnet - Plurilock
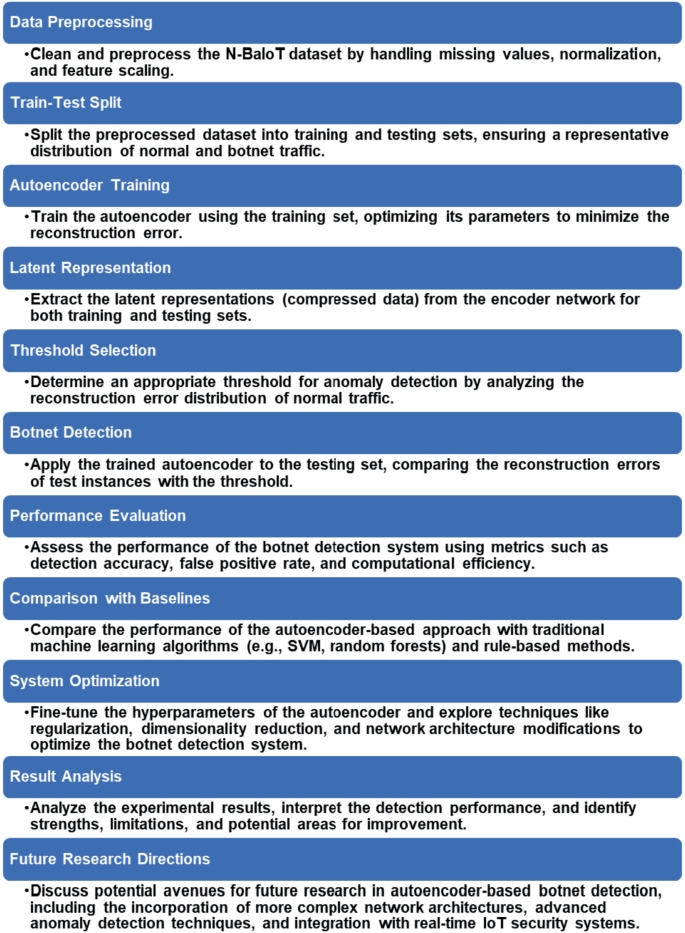
Autoencoder-Based Botnet Detection for Enhanced IoT Security

Learn the IoT botnets basics every IT expert should know
Recomendado para você
-
 Evades.io (Tutorial) // How to use new accessories with Requestly extension04 julho 2024
Evades.io (Tutorial) // How to use new accessories with Requestly extension04 julho 2024 -
 Evades io — Play for free at04 julho 2024
Evades io — Play for free at04 julho 2024 -
 Engineered vector evades photoreceptor pathology and microglia and CD804 julho 2024
Engineered vector evades photoreceptor pathology and microglia and CD804 julho 2024 -
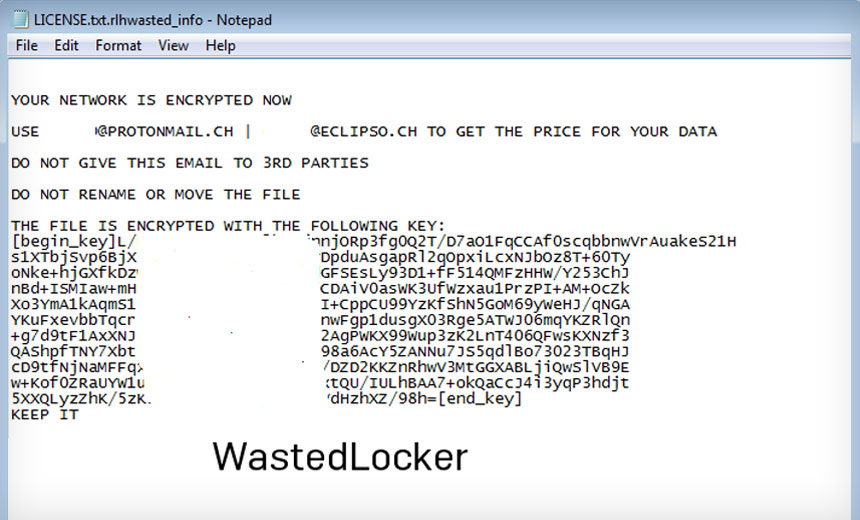 How WastedLocker Evades Anti-Ransomware Tools04 julho 2024
How WastedLocker Evades Anti-Ransomware Tools04 julho 2024 -
 Evades.io Handbook #2: How To Break with Brute04 julho 2024
Evades.io Handbook #2: How To Break with Brute04 julho 2024 -
 Evades.io04 julho 2024
Evades.io04 julho 2024 -
GitHub - Neondertalec/tsmod04 julho 2024
-
 Specialized S-Works Evade Ii Angi Mips Sagan Ltd Helmet – Incycle04 julho 2024
Specialized S-Works Evade Ii Angi Mips Sagan Ltd Helmet – Incycle04 julho 2024 -
 Specialized Evade 204 julho 2024
Specialized Evade 204 julho 2024 -
 Biomolecules, Free Full-Text04 julho 2024
Biomolecules, Free Full-Text04 julho 2024
você pode gostar
-
 Pretty good starting 3?? : r/StateOfDecay04 julho 2024
Pretty good starting 3?? : r/StateOfDecay04 julho 2024 -
 Spiders : r/Slipknot04 julho 2024
Spiders : r/Slipknot04 julho 2024 -
 Argentina - CA Brown de Adrogué - Results, fixtures, squad04 julho 2024
Argentina - CA Brown de Adrogué - Results, fixtures, squad04 julho 2024 -
 My Hero Academia confirma quantos episódios terá a sua quinta temporada - Critical Hits04 julho 2024
My Hero Academia confirma quantos episódios terá a sua quinta temporada - Critical Hits04 julho 2024 -
![Rayquaza EX (Shiny) [XY Promos]](https://pokemonplug.com/cdn/shop/products/108599.jpg?v=1660582203) Rayquaza EX (Shiny) [XY Promos]04 julho 2024
Rayquaza EX (Shiny) [XY Promos]04 julho 2024 -
 Swords by Skyknightb on DeviantArt04 julho 2024
Swords by Skyknightb on DeviantArt04 julho 2024 -
 FIGURINHAS LEGEND E ROOKIE DO ÁLBUM DA COPA 2023?04 julho 2024
FIGURINHAS LEGEND E ROOKIE DO ÁLBUM DA COPA 2023?04 julho 2024 -
 Star Citizen shows off new ships and offers vague details of ship release timing04 julho 2024
Star Citizen shows off new ships and offers vague details of ship release timing04 julho 2024 -
 Haikyuu!! Season 2 - 21 - Lost in Anime04 julho 2024
Haikyuu!! Season 2 - 21 - Lost in Anime04 julho 2024 -
 anime of vampire hunter d versus lucent from alucard, Stable Diffusion04 julho 2024
anime of vampire hunter d versus lucent from alucard, Stable Diffusion04 julho 2024