Hack Attacks Testing How to Conduct Your - Back to Home
Por um escritor misterioso
Last updated 19 maio 2024

Hack Attacks Testing How to Conduct Your - Back to Home

Inside Mirai, the Hack that Broke the Internet
17 Best Penetration Testing Tools For Security Testing
How to hack an app: 8 best practices for pen testing mobile apps

Hack-back legislation: What your security team needs to know
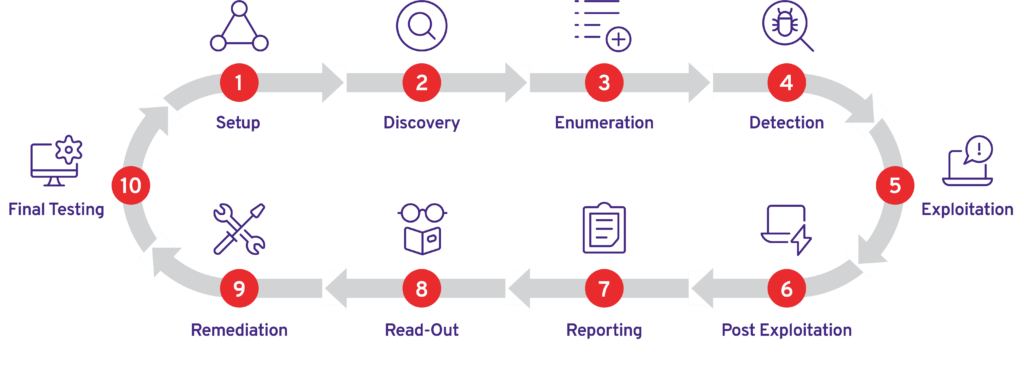
Hack the 10 Steps of the Pentesting Routine - PlexTrac
What is Penetration Testing and How Does It Work?

15 Surprisingly Hackable Things at Work

10 Most Common Types of Cyber Attacks Today - CrowdStrike
JavaScript for Hacking Made Easy: The Expert Guide on Security
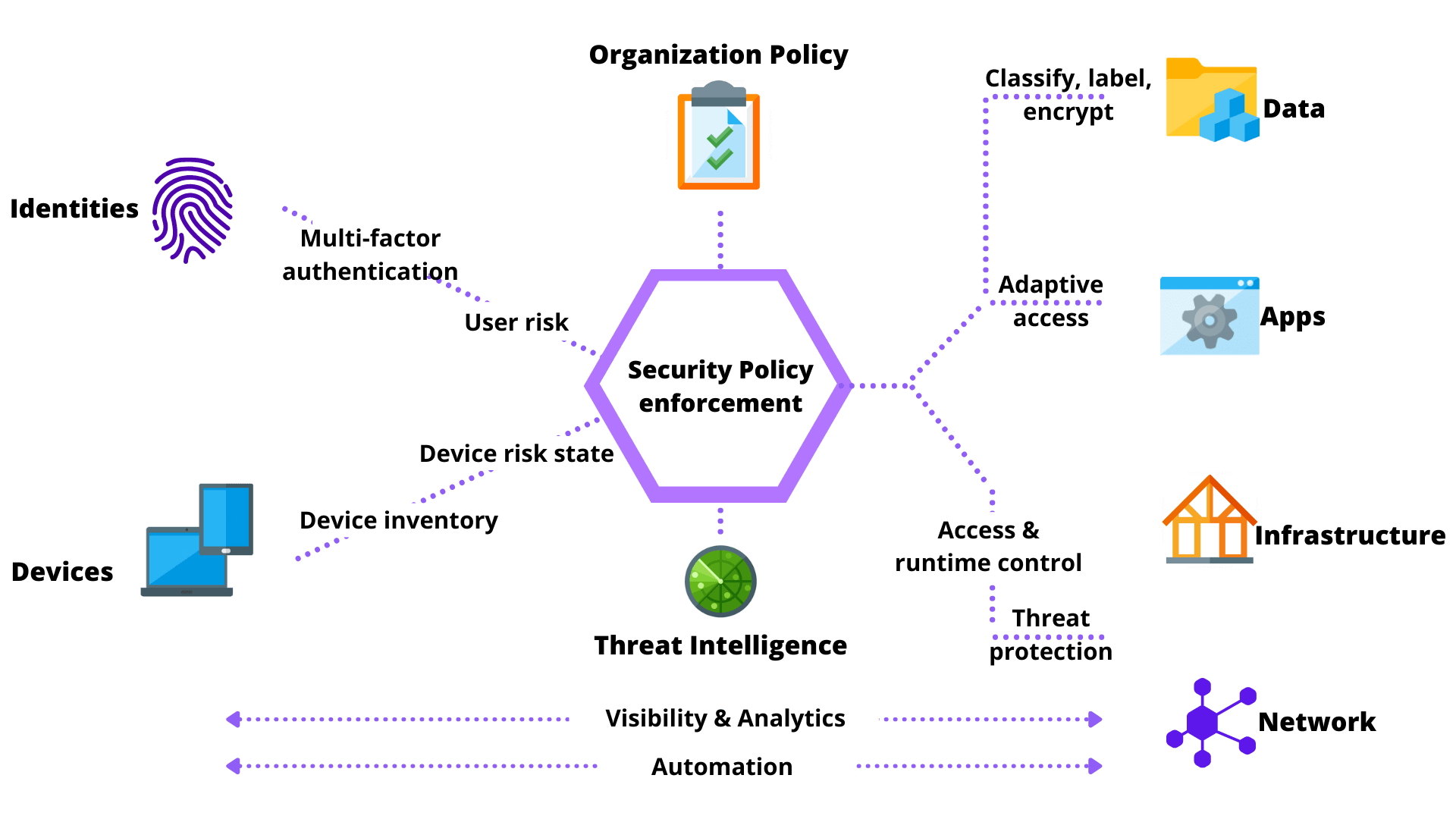
2023 Cyber Security Statistics: The Ultimate List Of Stats, Data & Trends

Complete Guide for Hacked Websites: How to Fix and Prevent It

The 27 Most Notorious Hacks History
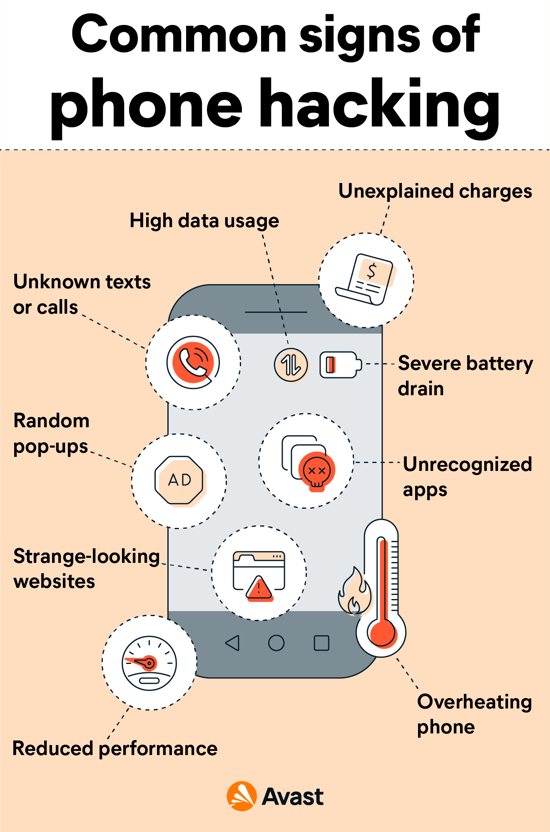
10 Signs That Your Phone Has Been Hacked
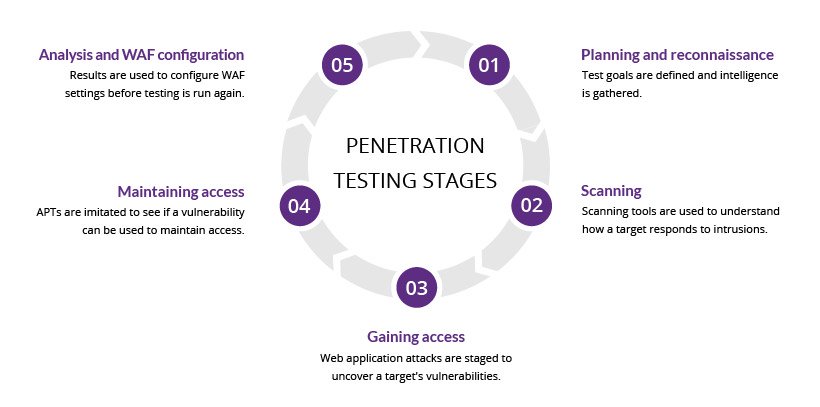
What is Penetration Testing, Step-By-Step Process & Methods
Recomendado para você
-
 Bitcoin #170 - Coinopolys19 maio 2024
Bitcoin #170 - Coinopolys19 maio 2024 -
 CryptoPunkets #891 - CryptoPunkets19 maio 2024
CryptoPunkets #891 - CryptoPunkets19 maio 2024 -
 PDF) Transforming Culture in the Digital Age19 maio 2024
PDF) Transforming Culture in the Digital Age19 maio 2024 -
Bitcoin #0626 - Bit_coin19 maio 2024
-
 L5.png19 maio 2024
L5.png19 maio 2024 -
 Crypto Skulls (Free NFT) #12003 - Crypto Skulls Fantasy19 maio 2024
Crypto Skulls (Free NFT) #12003 - Crypto Skulls Fantasy19 maio 2024 -
 AirJapan World Airline News19 maio 2024
AirJapan World Airline News19 maio 2024 -
 Nikonians News & Blogs: Interviews, Talkshows, News and More19 maio 2024
Nikonians News & Blogs: Interviews, Talkshows, News and More19 maio 2024 -
 Furnace Company Aurora East IL, Furnace Technician19 maio 2024
Furnace Company Aurora East IL, Furnace Technician19 maio 2024 -
 ICQ - Download19 maio 2024
ICQ - Download19 maio 2024
você pode gostar
-
Se o GTA é conhecido por jogar como um personagem que viola a lei, existe um jogo ou mecânica de jogo semelhante em que o jogador segue a lei? - Quora19 maio 2024
-
 What is Dave Bautista's net worth and how many times has he been19 maio 2024
What is Dave Bautista's net worth and how many times has he been19 maio 2024 -
 Caminhão Parking Simulador 3D - app android - AllBestApps19 maio 2024
Caminhão Parking Simulador 3D - app android - AllBestApps19 maio 2024 -
![FireRed hack: - Pokemon Sun Sky and Moon Galaxy [COMPLETED]](https://1.bp.blogspot.com/-BMYSPbJFgm0/X1zDCAz0_CI/AAAAAAAAIRk/594ZFXueEXcUM-k7yaJG_1rgbCd9EPJzwCLcBGAsYHQ/s1280/20200910_125229.jpg) FireRed hack: - Pokemon Sun Sky and Moon Galaxy [COMPLETED]19 maio 2024
FireRed hack: - Pokemon Sun Sky and Moon Galaxy [COMPLETED]19 maio 2024 -
 More goofy ahh Alphabet Lore doodles : r/alphabetfriends19 maio 2024
More goofy ahh Alphabet Lore doodles : r/alphabetfriends19 maio 2024 -
 otome game no hametsu flag en Instagram: “(。•̀ᴗ-)✧💕(♡ω♡ ) ~♪ ❥Artist / MUTTON ⟵ ______**•̩̩͙✩•̩̩͙*˚ ˚*•̩̩…19 maio 2024
otome game no hametsu flag en Instagram: “(。•̀ᴗ-)✧💕(♡ω♡ ) ~♪ ❥Artist / MUTTON ⟵ ______**•̩̩͙✩•̩̩͙*˚ ˚*•̩̩…19 maio 2024 -
 Conversion of sensitivity from 2D to 3D windows - General Gaming Discussion - Mouse Sensitivity Community19 maio 2024
Conversion of sensitivity from 2D to 3D windows - General Gaming Discussion - Mouse Sensitivity Community19 maio 2024 -
 dancing stick man on Make a GIF19 maio 2024
dancing stick man on Make a GIF19 maio 2024 -
 Jogo PS3 Ultra Street Fighter IV19 maio 2024
Jogo PS3 Ultra Street Fighter IV19 maio 2024 -
Jenny Wakeman(My life As A Teenage Robot) - Pretty dope.19 maio 2024
