Malware analysis Malicious activity
Por um escritor misterioso
Last updated 07 julho 2024

Malware Analysis: Protecting Your Network from Cyber Attacks
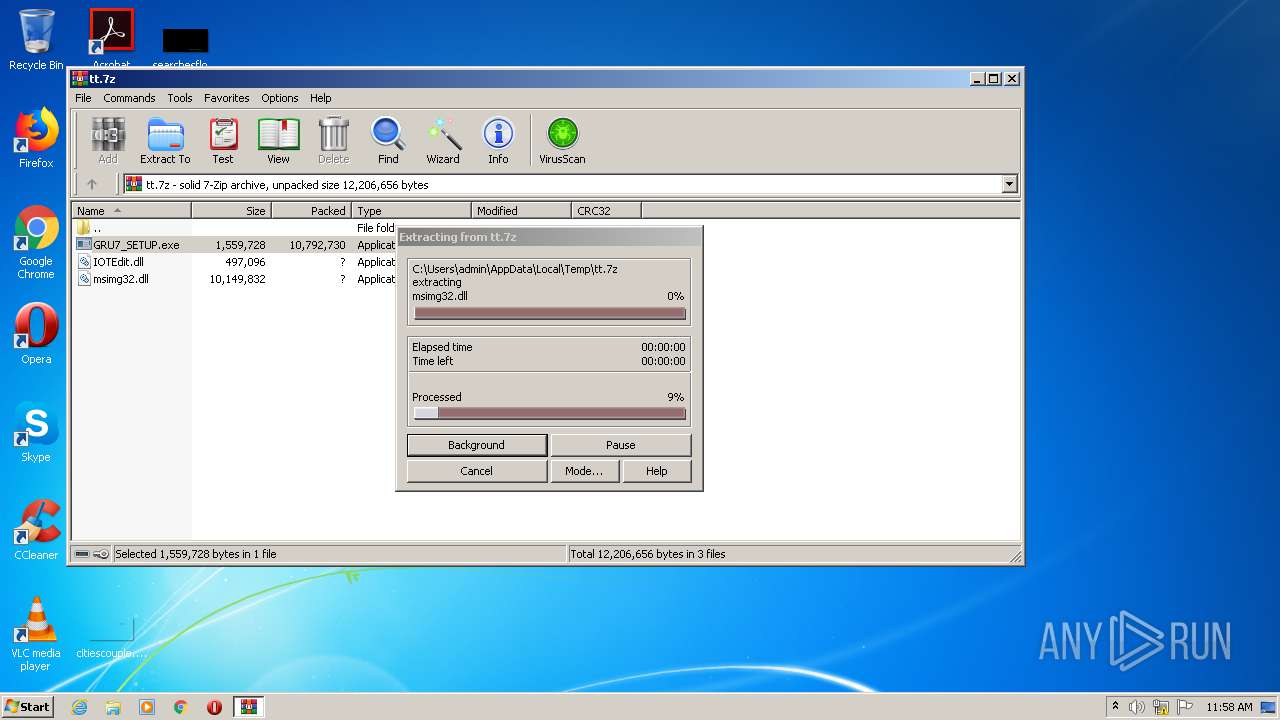
Malware analysis tt.7z Malicious activity
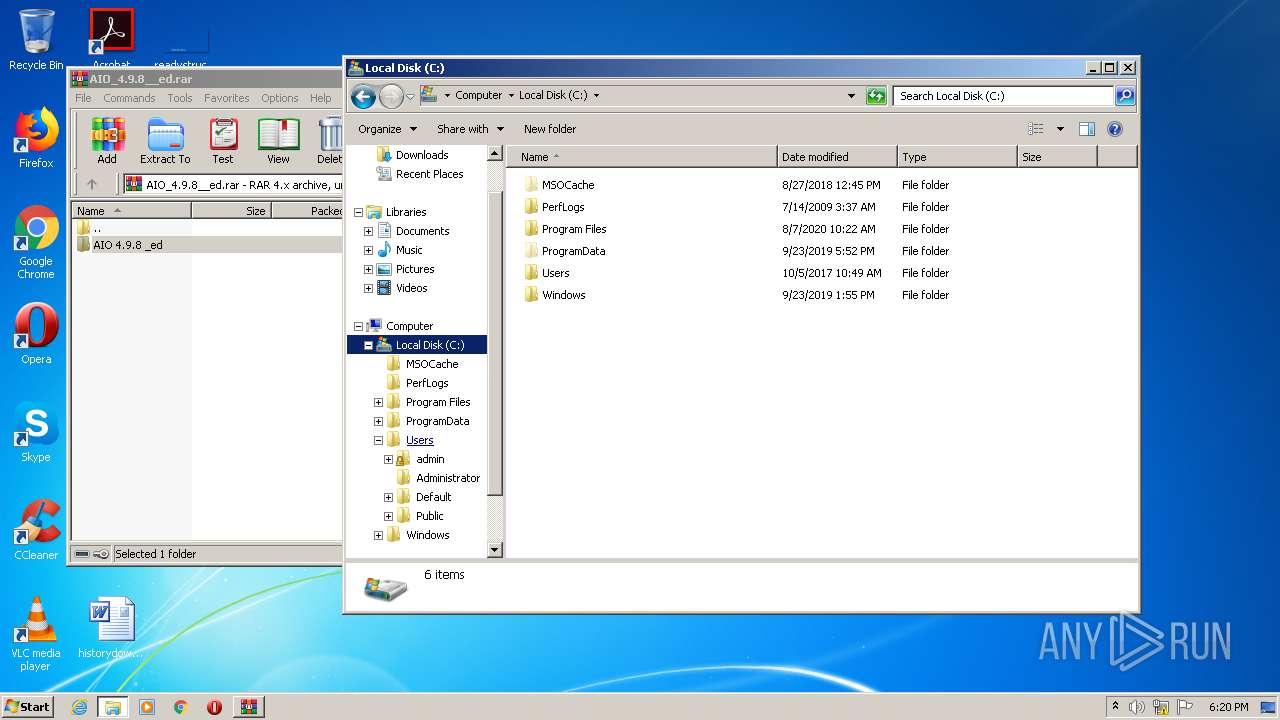
Malware analysis AIO_4.9.8__ed.rar Malicious activity

Malware analysis mykey_.rar Malicious activity
Interactive Online Malware Sandbox

AV-TEST Confirms Skyhigh Security Service Edge Delivers Superior Threat Protection in All Test Categories

Security Orchestration Use Case: Automating Malware Analysis - Palo Alto Networks Blog

TryHackMe Hacktivities

Malware Analysis: Steps & Examples - CrowdStrike

Malware analysis index.html Malicious activity

Malware Analysis: Steps & Examples - CrowdStrike

AlienVault - Open Threat Exchange

What is Malware? Definition, Types, Prevention - TechTarget
Recomendado para você
-
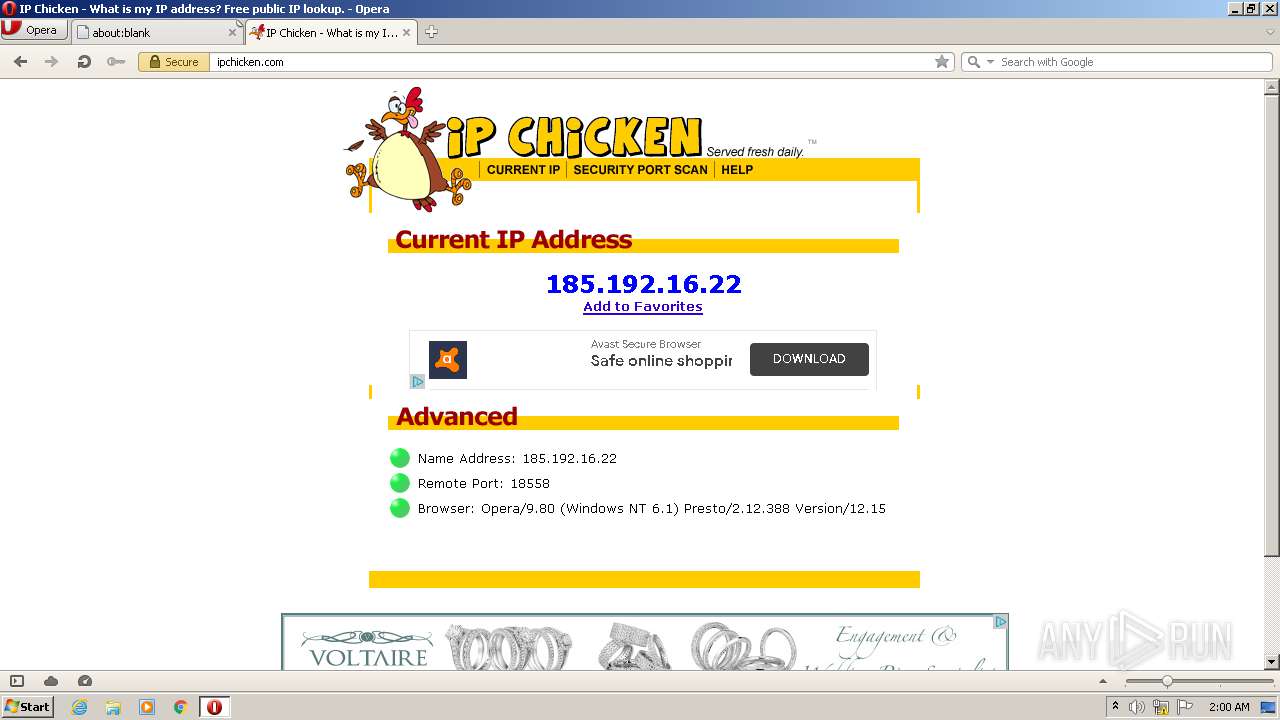
 How to extract your outside IP address - What's My IP - IP Chicken - IP Monkey07 julho 2024
How to extract your outside IP address - What's My IP - IP Chicken - IP Monkey07 julho 2024 -
![🔴LIVE] How to know my Local PC IP address?](https://i.ytimg.com/vi/HbDJUHhXKhg/maxresdefault.jpg) 🔴LIVE] How to know my Local PC IP address?07 julho 2024
🔴LIVE] How to know my Local PC IP address?07 julho 2024 -
 8 Sites That Show Your IP Address –07 julho 2024
8 Sites That Show Your IP Address –07 julho 2024 -
![Question] How to get around VPN blockers?](https://i.gyazo.com/f0c5d0d5b114f0d49954a16dd5112ac7.png) Question] How to get around VPN blockers?07 julho 2024
Question] How to get around VPN blockers?07 julho 2024 -
 chicken Memes & GIFs - Imgflip07 julho 2024
chicken Memes & GIFs - Imgflip07 julho 2024 -
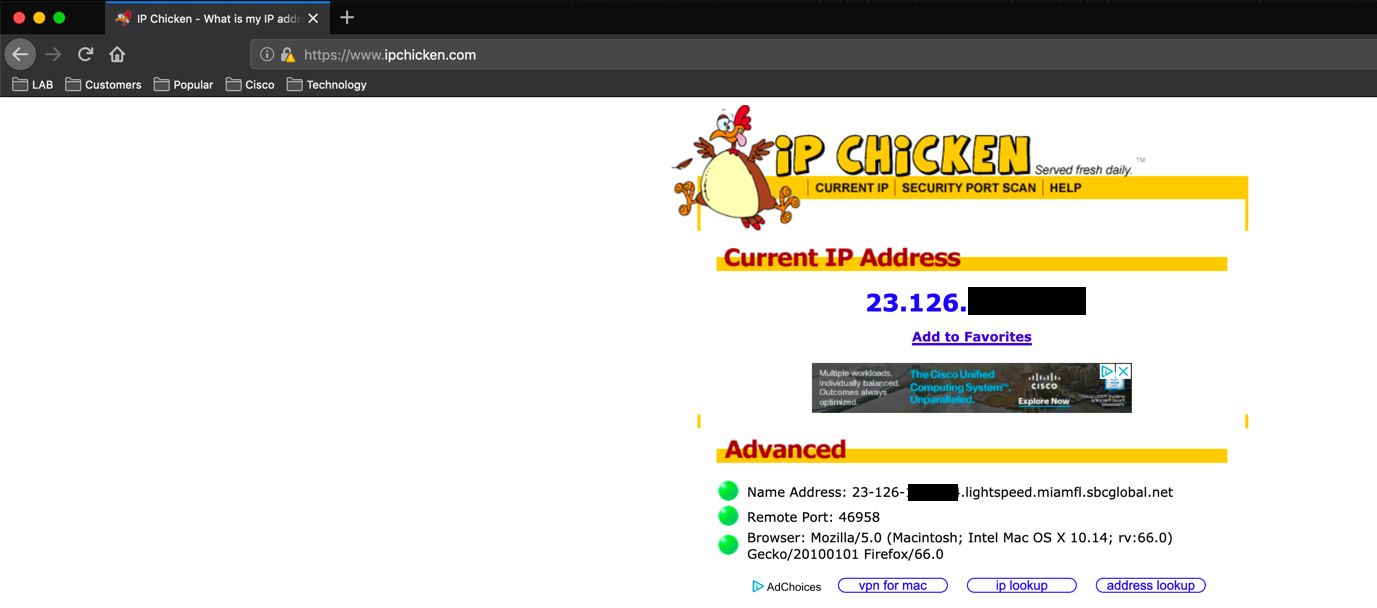 Troubleshooting NAT on Fortigate Firewall – InfoSec Monkey07 julho 2024
Troubleshooting NAT on Fortigate Firewall – InfoSec Monkey07 julho 2024 -
Ethical Hacking With Net07 julho 2024
-
Gogo's T-Mobile sponsored in-flight wifi? Free? On a PC?!07 julho 2024
-
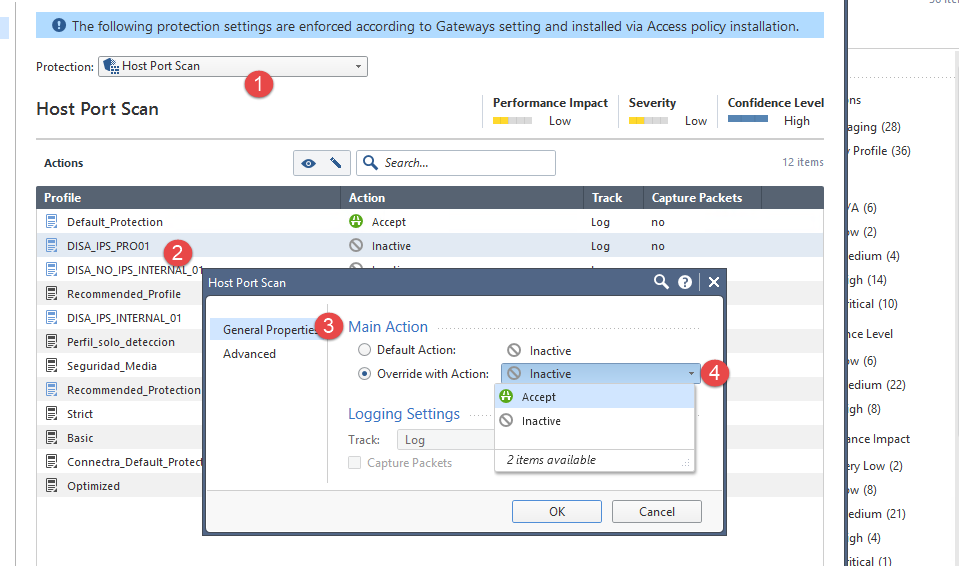 How can I avoid Host Port scan? - Check Point CheckMates07 julho 2024
How can I avoid Host Port scan? - Check Point CheckMates07 julho 2024 -
 Virtualizing pfSense Firewall on Synology DSM Virtual Machine Manager07 julho 2024
Virtualizing pfSense Firewall on Synology DSM Virtual Machine Manager07 julho 2024
você pode gostar
-
 Plane Crash/Shark Movie From '47 Meters Down' Execs 'No Way Up07 julho 2024
Plane Crash/Shark Movie From '47 Meters Down' Execs 'No Way Up07 julho 2024 -
 Onde assistir Breaking Bad? Sites para encontrar a série07 julho 2024
Onde assistir Breaking Bad? Sites para encontrar a série07 julho 2024 -
 Independiente del Valle, inspirado en Avellaneda y un ejemplo en formación vinculado a Qatar - TyC Sports07 julho 2024
Independiente del Valle, inspirado en Avellaneda y un ejemplo en formación vinculado a Qatar - TyC Sports07 julho 2024 -
 Spiders (System of a Down) by D. Malakian, J. Dolmayan, S. Tankian, S. Odadjian on MusicaNeo07 julho 2024
Spiders (System of a Down) by D. Malakian, J. Dolmayan, S. Tankian, S. Odadjian on MusicaNeo07 julho 2024 -
 Netflix's 'The Ballad of Buster Scruggs' Doesn't Add Up - The Atlantic07 julho 2024
Netflix's 'The Ballad of Buster Scruggs' Doesn't Add Up - The Atlantic07 julho 2024 -
Steam Workshop::Shogi07 julho 2024
-
Gigantes da Europa F.C07 julho 2024
-
 How To Find All 12 Rare Eggs In Roblox Murder Mystery 207 julho 2024
How To Find All 12 Rare Eggs In Roblox Murder Mystery 207 julho 2024 -
 Guia PANROTAS - Edição 291 - Junho/1997 by PANROTAS Editora - Issuu07 julho 2024
Guia PANROTAS - Edição 291 - Junho/1997 by PANROTAS Editora - Issuu07 julho 2024 -
 how to add a pass to please donate pc|TikTok Search07 julho 2024
how to add a pass to please donate pc|TikTok Search07 julho 2024