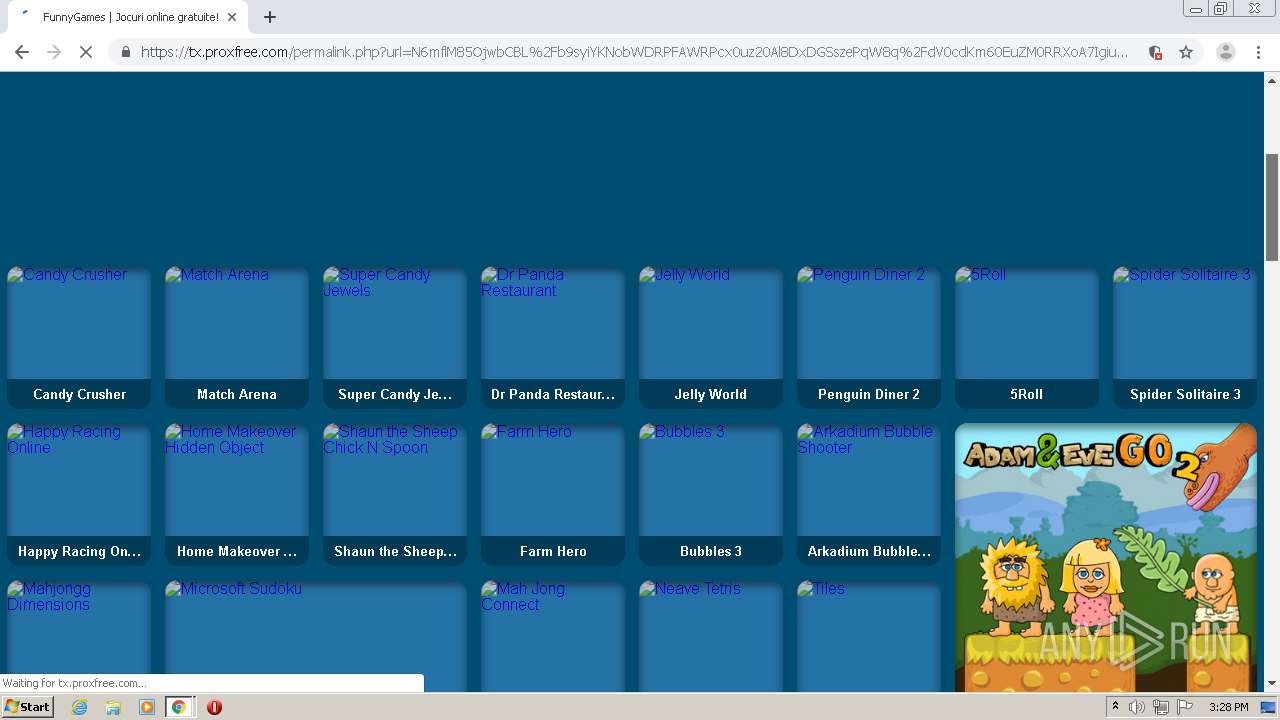
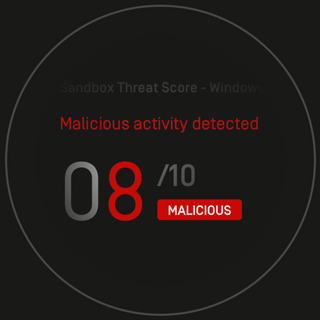
Malware analysis Malicious activity
Por um escritor misterioso
Last updated 08 junho 2024
MetaDefender Cloud Advanced threat prevention and detection

Mastering Malware Analysis

Info stealers and how to protect against them

MetaDefender Cloud Advanced threat prevention and detection
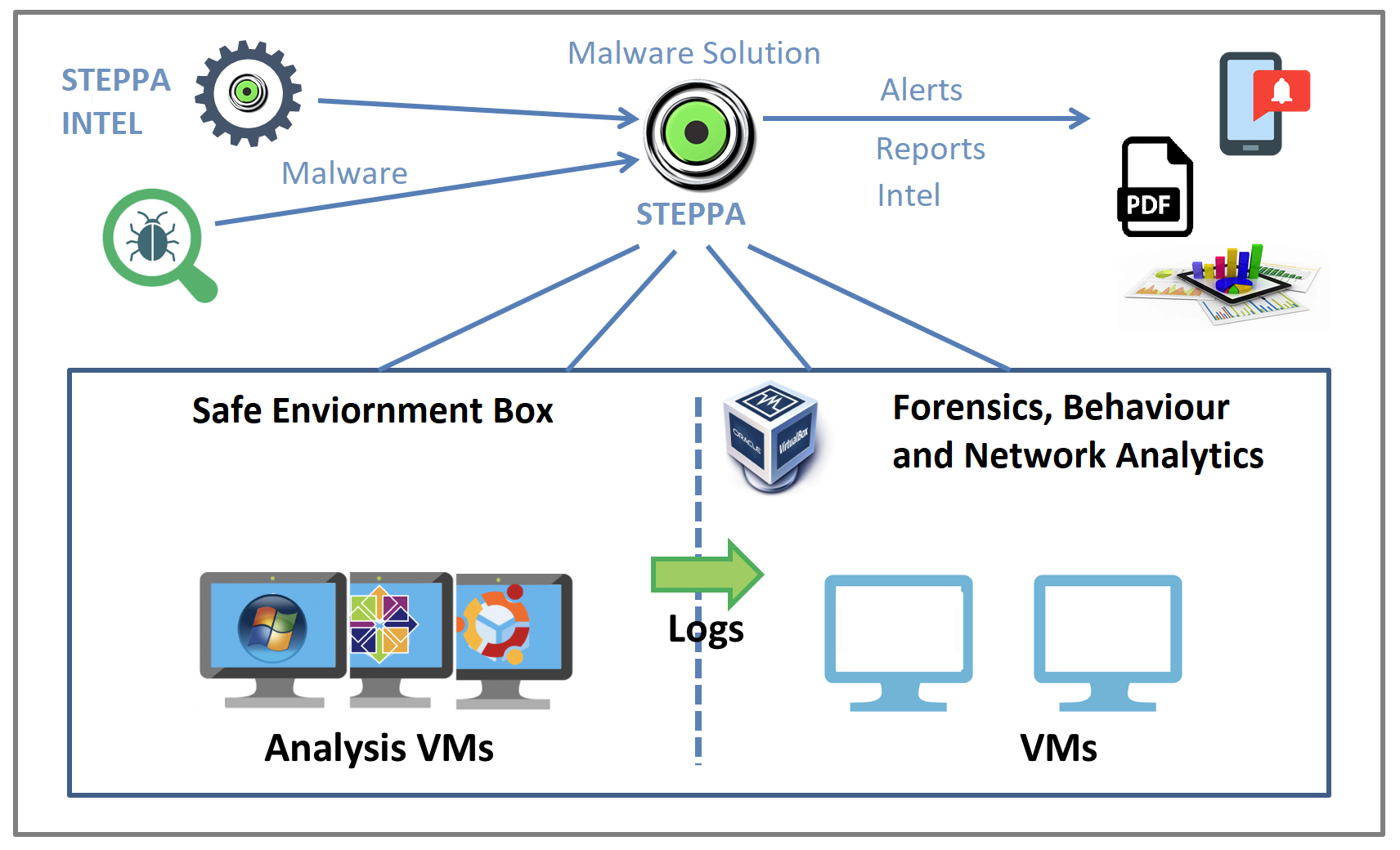
Malware Analysis Solution: Analyze, Detect, and Protect
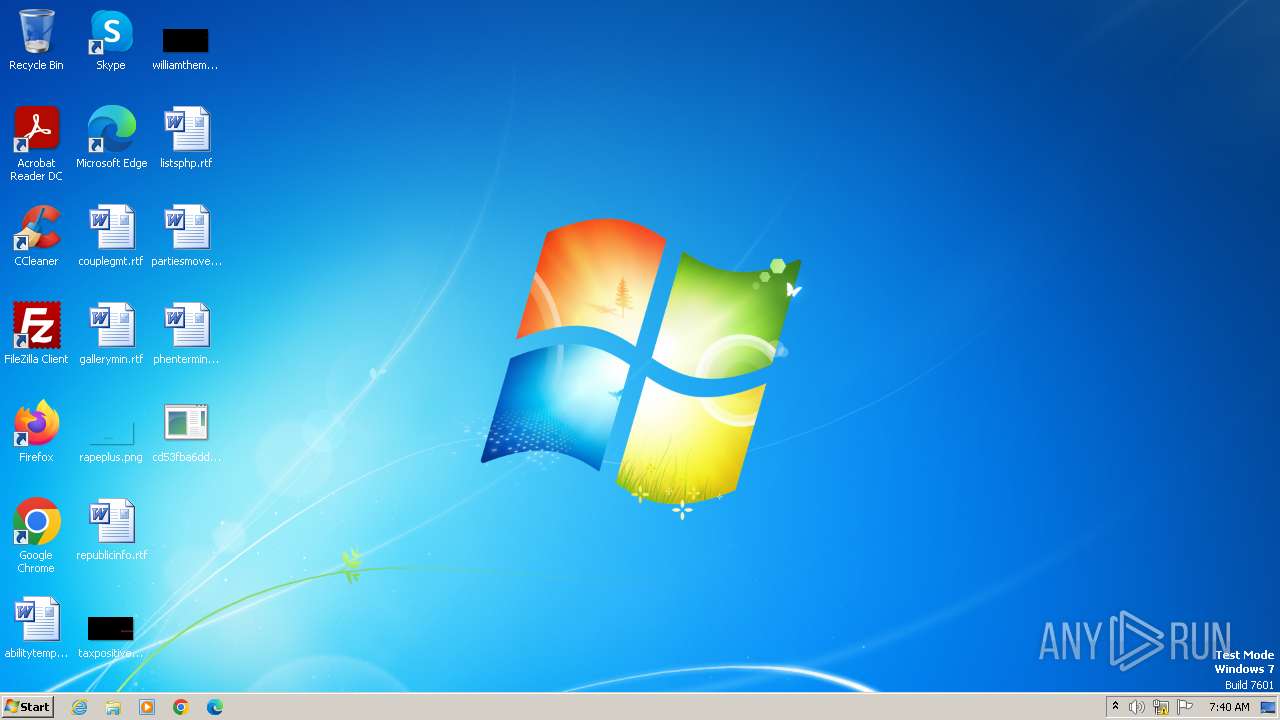
Malware analysis cd53fba6ddd4ae4ef7a5747c6003236c85791477854cc1b7ce00e0f8ee7677d9 Malicious activity

Dynamic malware analysis [34]

Building A Simple Malware Analysis Pipeline In The Homelab Pt - 1 · Arch Cloud Labs

Playbook of the Week: Malware Investigation and Response - Palo Alto Networks Blog
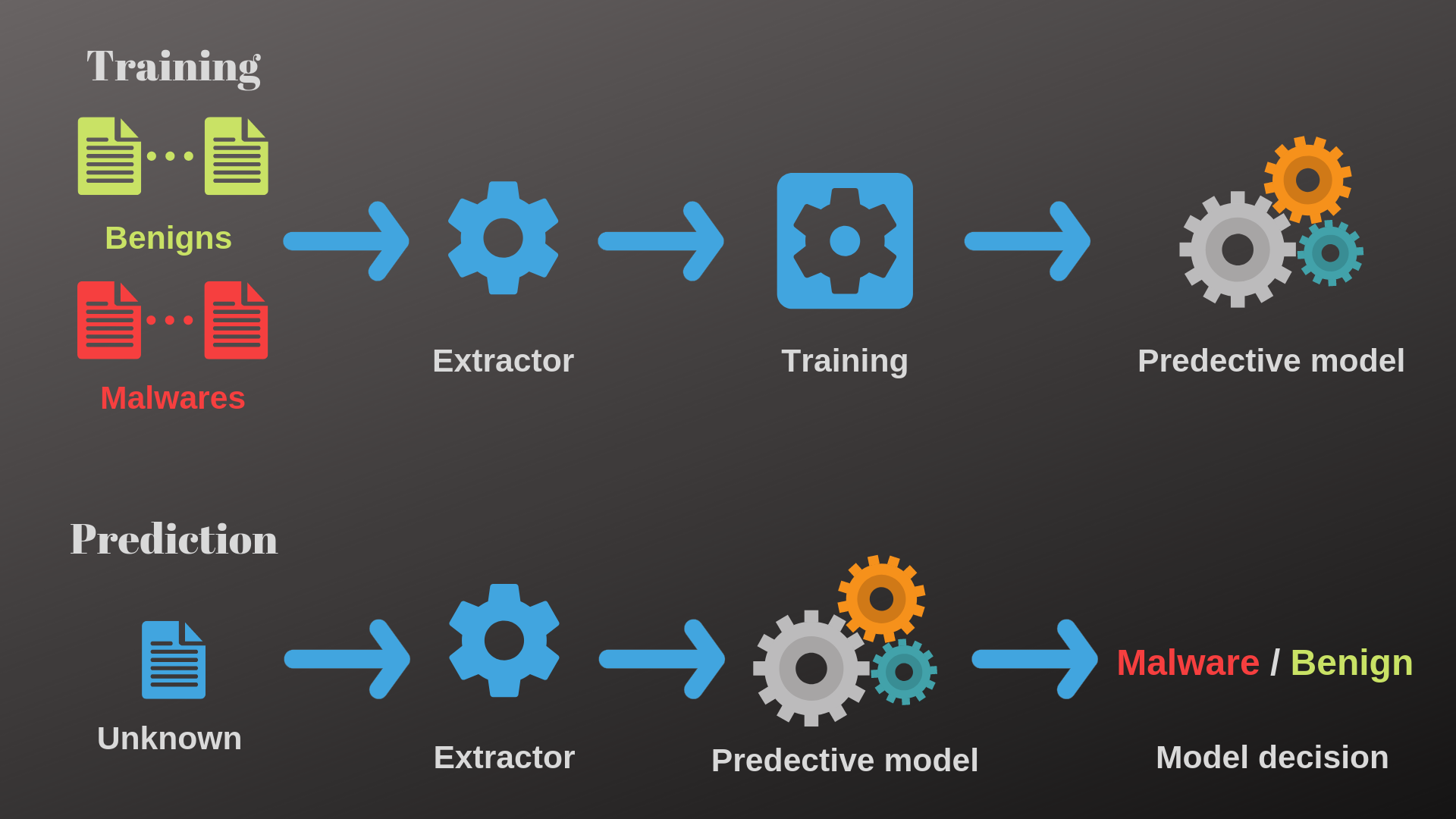
Feature Extraction and Detection of Malwares Using Machine Learning
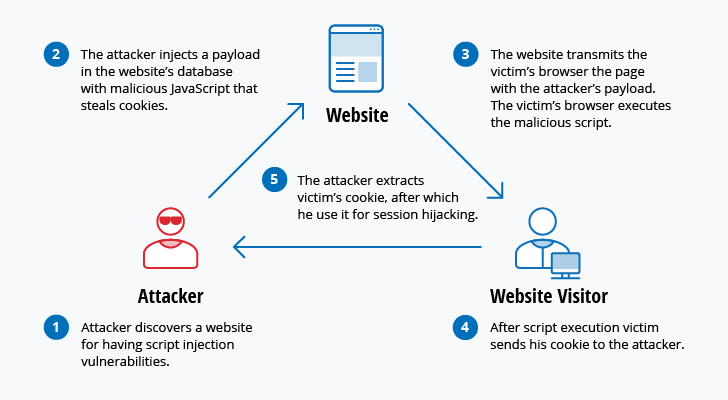
The 12 Most Common Types of Cybersecurity Attacks Today
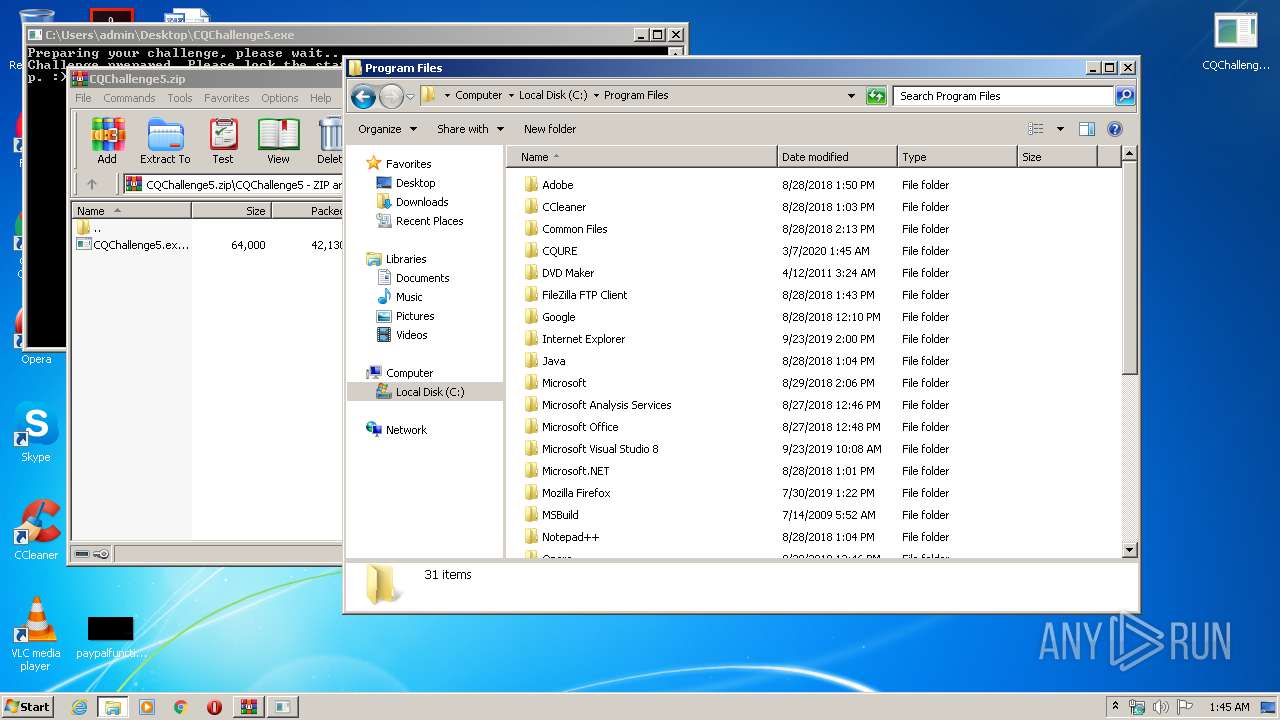
Malware analysis CQChallenge5.zip Malicious activity

Malware Analysis: Steps & Examples - CrowdStrike
Malicious URL Scanner, Scan URLs for Malware
Recomendado para você
-
 Bubbles 3 - Free Play & No Download08 junho 2024
Bubbles 3 - Free Play & No Download08 junho 2024 -
 Bubble Shooter Game – veerublog08 junho 2024
Bubble Shooter Game – veerublog08 junho 2024 -
 funnygames.nu - Play free online games! - Funny Games08 junho 2024
funnygames.nu - Play free online games! - Funny Games08 junho 2024 -
 17,106 Funny Games Stock Photos - Free & Royalty-Free Stock Photos from Dreamstime08 junho 2024
17,106 Funny Games Stock Photos - Free & Royalty-Free Stock Photos from Dreamstime08 junho 2024 -
 Premium Vector Children active games infographic with funny games round dances hopscotch board and catch up games descriptions vector illustration08 junho 2024
Premium Vector Children active games infographic with funny games round dances hopscotch board and catch up games descriptions vector illustration08 junho 2024 -
 Bubble Shooter Gameplay #2508 junho 2024
Bubble Shooter Gameplay #2508 junho 2024 -
 Kaeru San - Sad baby blowing nose bubbles www funny funny pictures08 junho 2024
Kaeru San - Sad baby blowing nose bubbles www funny funny pictures08 junho 2024 -
 Bubble Shield Sprite Sheets Sprite, Indie game development08 junho 2024
Bubble Shield Sprite Sheets Sprite, Indie game development08 junho 2024 -
 Bubble Game 308 junho 2024
Bubble Game 308 junho 2024 -
 Websites neighbouring Funnygames.com.mx08 junho 2024
Websites neighbouring Funnygames.com.mx08 junho 2024
você pode gostar
-
 BEYBLADE Burst Evolution Trio Spryzen 3-Pack; Legend Spryzen S3, Lord Spryzen S5, Spryzen S2 Balance-Type Battling Game Top Toys : Toys & Games08 junho 2024
BEYBLADE Burst Evolution Trio Spryzen 3-Pack; Legend Spryzen S3, Lord Spryzen S5, Spryzen S2 Balance-Type Battling Game Top Toys : Toys & Games08 junho 2024 -
 Ahsoka review: A delightful treat for some fans, but just another08 junho 2024
Ahsoka review: A delightful treat for some fans, but just another08 junho 2024 -
 8 top live chat apps for your website in 202408 junho 2024
8 top live chat apps for your website in 202408 junho 2024 -
 Max Payne 3 PS4|TikTok Search08 junho 2024
Max Payne 3 PS4|TikTok Search08 junho 2024 -
 Prtty much evry bordr gam evr by HappyBoomBox on DeviantArt08 junho 2024
Prtty much evry bordr gam evr by HappyBoomBox on DeviantArt08 junho 2024 -
 Jogo De Xadrez Bruxo Tabuleiro Jogo Completo Medieval Resina08 junho 2024
Jogo De Xadrez Bruxo Tabuleiro Jogo Completo Medieval Resina08 junho 2024 -
![Getnet Argentina para WooCommerce] Reviews](https://ps.w.org/integrar-getnet-con-woo/assets/icon-256x256.png?rev=2863651) Getnet Argentina para WooCommerce] Reviews08 junho 2024
Getnet Argentina para WooCommerce] Reviews08 junho 2024 -
 How to Awaken Light in Blox Fruits - Player Assist08 junho 2024
How to Awaken Light in Blox Fruits - Player Assist08 junho 2024 -
 78 Gacha ideas clothing sketches, club outfit ideas, manga clothes08 junho 2024
78 Gacha ideas clothing sketches, club outfit ideas, manga clothes08 junho 2024 -
 Rockstar_Foxy_And_pickles on Game Jolt: My withered Foxy08 junho 2024
Rockstar_Foxy_And_pickles on Game Jolt: My withered Foxy08 junho 2024