Malware analysis Suspicious activity
Por um escritor misterioso
Last updated 05 julho 2024
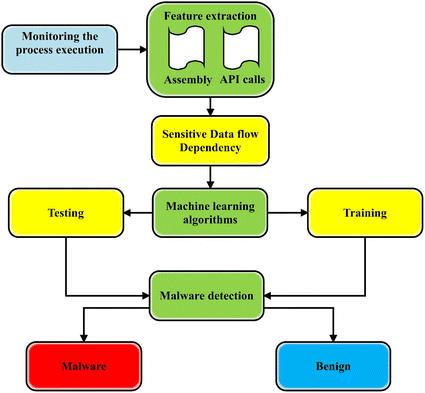
A state-of-the-art survey of malware detection approaches using

Intro to Malware Analysis: What It Is & How It Works - InfoSec

Using Python for Malware Analysis — A Beginners Guide

Malware Analysis Benefits Incident Response

A flow chart of malware detection approaches and features
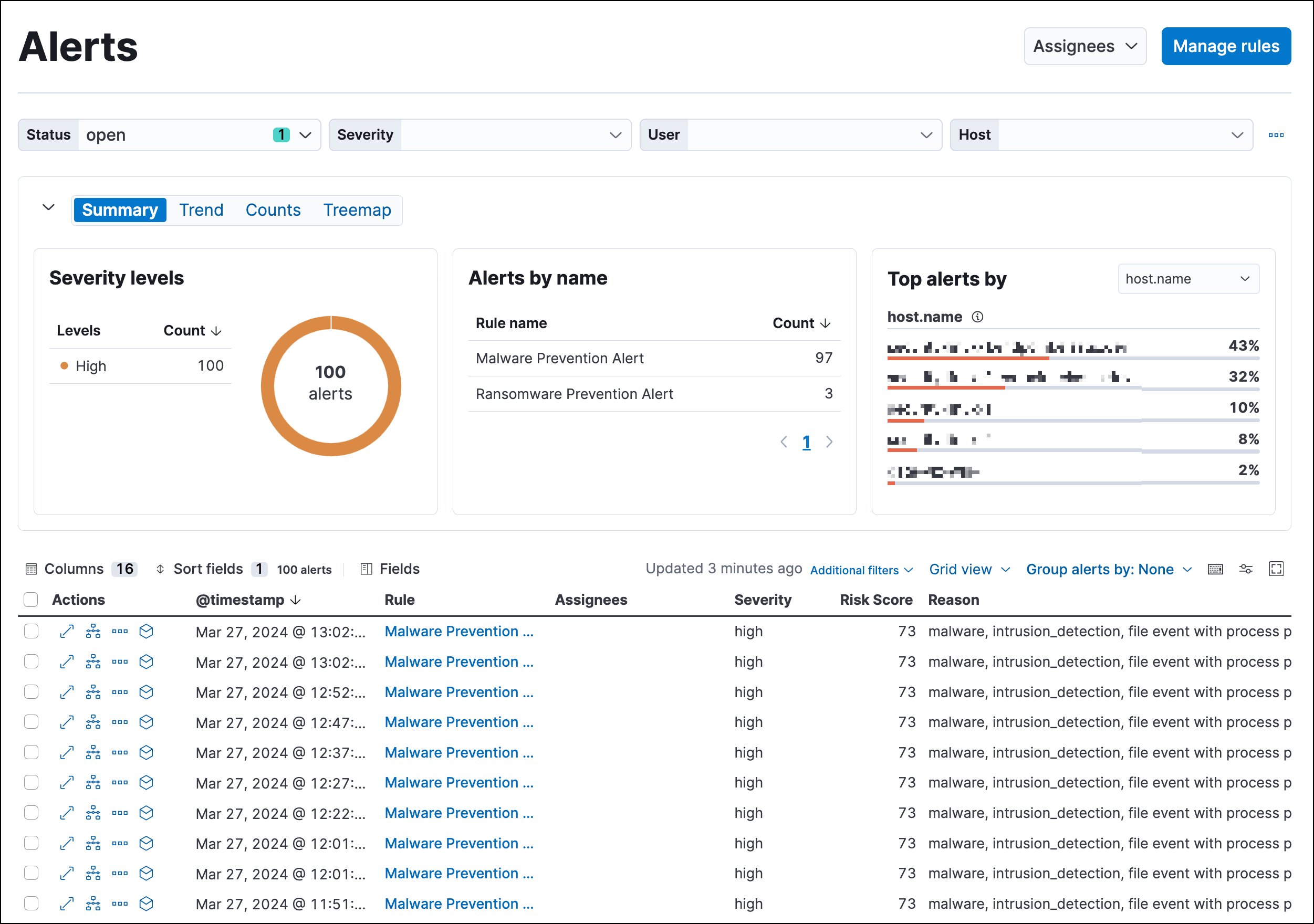
Detections and alerts, Elastic Security Solution [8.11]

Ransomware: How it Works & How to Remove It

Malware Detection & Top Techniques Today

10 Best Malware Analysis Tools - Updated 2023! (Paid & Free)
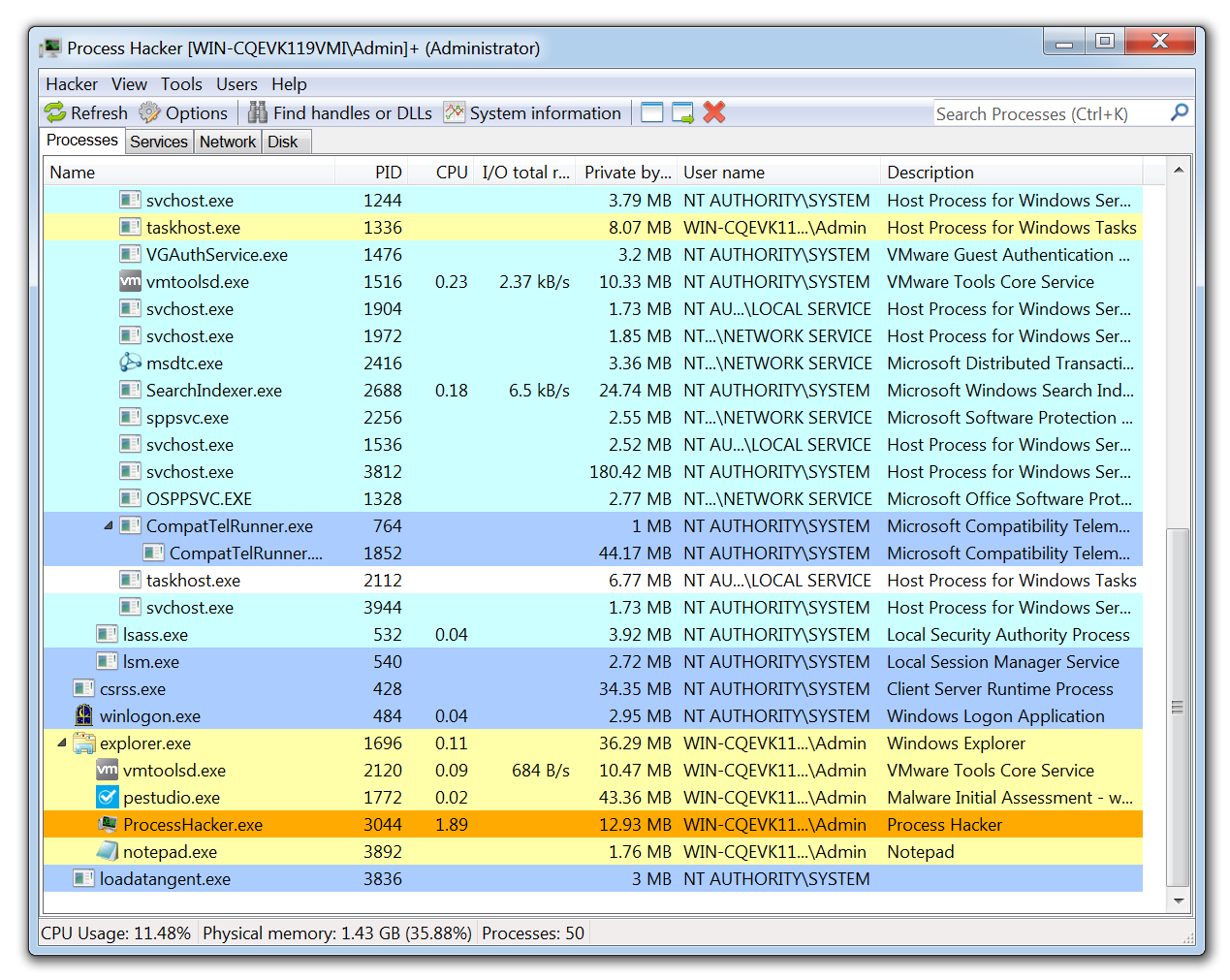
11 Best Malware Analysis Tools and Their Features

Behavioral blocking and containment: Transforming optics into

Malware Incident Response Steps on Windows, and Determining If the

The General Behavior of Ransomware - Cisco Blogs
Recomendado para você
-
Roblox: criança de 7 anos tem personagem estuprada em jogo on-line05 julho 2024
-
 Roblox on the App Store05 julho 2024
Roblox on the App Store05 julho 2024 -
 How to Get Roblox Studio on iPad05 julho 2024
How to Get Roblox Studio on iPad05 julho 2024 -
HACKING!👨💻 Hacker Tycoon - Roblox05 julho 2024
-
 roblox-hacks · GitHub Topics · GitHub05 julho 2024
roblox-hacks · GitHub Topics · GitHub05 julho 2024 -
 Master mod menu for roblox APK for Android Download05 julho 2024
Master mod menu for roblox APK for Android Download05 julho 2024 -
Jailbreak - Roblox05 julho 2024
-
 hacker roblox download05 julho 2024
hacker roblox download05 julho 2024 -
MOD-MASTER for Roblox - Apps on Google Play05 julho 2024
-
 Roblox Hack Mod Menu 2023 Unlimited Roblox V2.574.243 Direct Link Mediafire05 julho 2024
Roblox Hack Mod Menu 2023 Unlimited Roblox V2.574.243 Direct Link Mediafire05 julho 2024
você pode gostar
-
como trocar nome de usuário no roblox|TikTok Search05 julho 2024
-
 MILF - Man I Love Floppa - Big Floppa Funny Meme Design - Milf Man I Love Floppa - Tapestry05 julho 2024
MILF - Man I Love Floppa - Big Floppa Funny Meme Design - Milf Man I Love Floppa - Tapestry05 julho 2024 -
 Call of Duty blocked on Xbox 'for a number years' by Sony PlayStation- claims Microsoft head Phil Spencer; and other latest updates05 julho 2024
Call of Duty blocked on Xbox 'for a number years' by Sony PlayStation- claims Microsoft head Phil Spencer; and other latest updates05 julho 2024 -
garry's mod apk mobile APK (Android Game) - Free Download05 julho 2024
-
 Haikyuu!! 3rd Season Opening Burnout Syndromes Hikari (Let the Light Shine) Sheet music for Piano (Solo)05 julho 2024
Haikyuu!! 3rd Season Opening Burnout Syndromes Hikari (Let the Light Shine) Sheet music for Piano (Solo)05 julho 2024 -
 Goth Leone : r/AkameGaKILL05 julho 2024
Goth Leone : r/AkameGaKILL05 julho 2024 -
 We do a little trolling in this beat boxing — THIS IS AN IMPORTANT05 julho 2024
We do a little trolling in this beat boxing — THIS IS AN IMPORTANT05 julho 2024 -
Nanoparticles for Oral Biofilm Treatments05 julho 2024
-
 ZVEZDA POBEDILA PRED LIGU ŠAMPIONA: Crveno-beli savladali05 julho 2024
ZVEZDA POBEDILA PRED LIGU ŠAMPIONA: Crveno-beli savladali05 julho 2024 -
 Vampire The Masquerade - Bloodlines Unofficial Patch - Download05 julho 2024
Vampire The Masquerade - Bloodlines Unofficial Patch - Download05 julho 2024



